
Summary
3.1 Installed program on the Exchange server 5
3.3 Get-OrganizationConfig | Select-Object Ews* 5
3.4 Get-CasMailbox jbon@cloudmenow.net | Select-Object Ews* 6
3.5 On Premise Autodiscover and Web Service test 6
3.7 Test-OutlookWebServices -identity jbon@cloudmenow.net -MailboxCredential $C [OK] 8
3.10 Invoke-RestMethod [OK] 11
3.11 Test-Federationtrust [OK] 11
3.12 Get-WebserviceVirtualDirectory -server EX1-SRv-01 | fl *auth* [OK] 12
3.14 Get-partnerApplication [OK] 14
3.15 Get-ADUser -Identity jbon -properties * 14
3.16 Set-Virtual directory Configuration 16
4.1 Get-OrganizationConfig | Select-Object Ews* 17
4.2 Teams calendar APP enabled 17
4.4 Get-federation Information 18
4.5 Get-OrganizationRelationship 18
4.6 Get-mailuser -identity « jean Bon » 18
4.8 Autodiscover Request in IIS WSC1 21
4.9 get-msoluser -UserPrincipalName jbon@cloudmenow.net | fl 22
4.10 Get-CsOnlineUser -Identity jbon@cloudmenow.net | fl 24
5.5 Free Busy Test with other EWS configuration 31
7.1.1 Set-OrganizationConfig 33
7.3.1 Comparing configuration 36
This article in PDF here : https://1drv.ms/b/s!AlKfEdbwpIS_iPw3i076hzW3Ivov8A?e=N8X4O2
-
introduction
Well, it’s been more than three days now that I’ve been trying to make it work so that a Teams client can display the calendar of an On premise mailbox. After more than 35 hours of work on a simplistic environment (no load balancer, no reverse proxy, only one Exchange server etc..) no way. The configuration has been reviewed dozens of times, we have changed and re-changed some settings, nothing happens. Online users can’t access on Premise calendars, and Teams is unable to retrieve the calendar from an on Premise mailbox.
You will find below the configuration used
-
Technical Articles
https://www.kpcs.cz/cs/novinky/blog/exchange-hybrid-a-microsoft-teams.html
-
OnPremiseConfiguration
Exchange server version
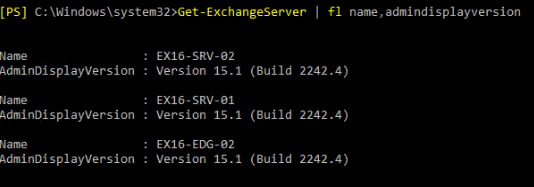
-
Installed program on the Exchange server
-
Teams version

-
Get-OrganizationConfig | Select-Object Ews*
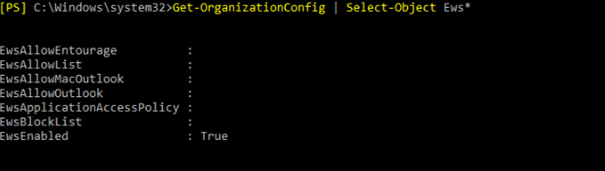
-
Get-CasMailbox jbon@cloudmenow.net | Select-Object Ews*
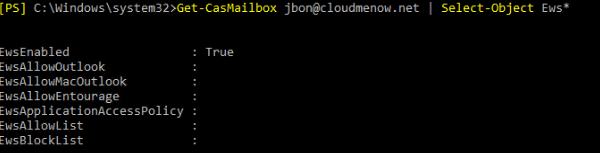
-
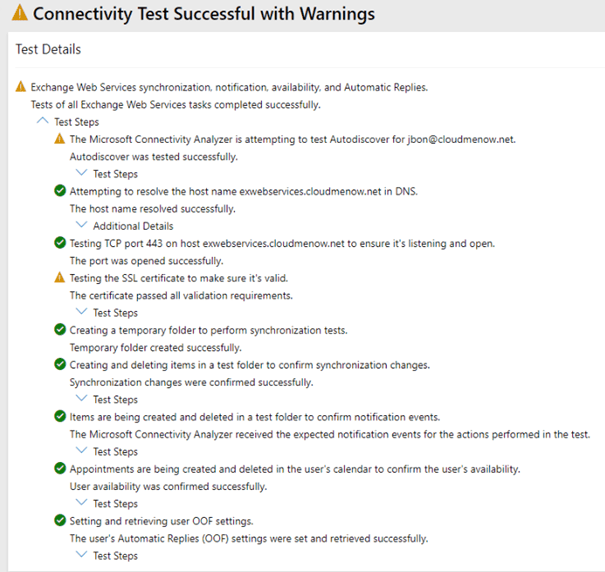
On Premise Autodiscover and Web Service test
-
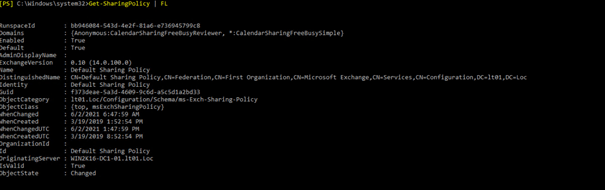
Get-SharingPolicy
If the free/busy problem persists, make sure that the sharing policies in the on-premises Exchange Server environment and in Exchange Online match. To determine this, run the following command in the Exchange Management Shell, and then note the value in the Domains field in the results:
-
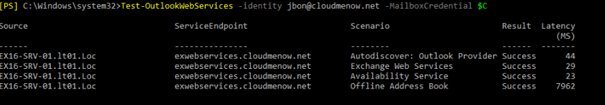
Test-OutlookWebServices -identity jbon@cloudmenow.net -MailboxCredential $C [OK]
-
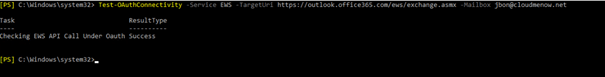
Test-OAuthConnectivity -Service EWS -TargetUri https://outlook.office365.com/ews/exchange.asmx -Mailbox jbon@cloudmenow.net [OK]
-
Test-OAuthConnectivity -Service EWS -TargetUri https://exwebservices.cloudmenow.net/metadata/json/1 -Mailbox CloudMailboxUser@cloudmelater.online -Verbose | Format-List [NONE OK]
RunspaceId : 0536bca5-4975-4e68-b865-1ed0e16326d5
Task : Checking EWS API Call Under Oauth
Detail : The configuration was last successfully loaded at 1/1/0001 12:00:00 AM UTC. This was 1062674647 minutes ago.
The token cache is being cleared because « use cached token » was set to false.
Exchange Outbound Oauth Log:
Client request ID: 1ab7109f-ce1d-4dd0-b36e-2f95ae35037f
Information:[OAuthCredentials:Authenticate] entering
Information:[OAuthCredentials:Authenticate] challenge from ‘https://exwebservices.cloudmenow.net/ews/Exchange.asmx’ received: Bearer client_id= »00000002-0000-0ff1-ce00-000000000000″,
trusted_issuers= »00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″, token_types= »app_asserted_user_v1 service_asserted_app_v1″,Basic realm= »exwebservices.cloudmenow.net »,Negotiate,NTLM
Information:[OAuthCredentials:GetToken] client-id: ‘00000002-0000-0ff1-ce00-000000000000’, realm: », trusted_issuer: ‘00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8’
Information:[OAuthCredentials:GetToken] Start building a token using organizationId ’41de3d62-e522-457d-af39-e4a9ecf064f8′
Information:[OAuthCredentials:GetToken] Start building a token using adUser
Information:[OAuthTokenBuilder:GetAppToken] start building the apptoken
Information:[OAuthTokenBuilder:GetAppToken] checking enabled auth servers
Information:[OAuthTokenBuilder:GetAppToken] trusted_issuer includes the auth server ‘MicrosoftSts’: 00000001-0000-0000-c000-000000000000@*,
Information:[OAuthTokenBuilder:GetAppToken] trying to get the apptoken from the auth server ‘MicrosoftSts’ for resource
‘00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8′, tenantId ’41de3d62-e522-457d-af39-e4a9ecf064f8’, userDomain ‘cloudmelater.online’
Information:[TokenCache:GetActorToken] Each key and its counts are L:00000002-0000-0ff1-ce00-000000000000-AS:00000001-0000-0000-c000-000000000000@*, 0
Information:[TokenCache:GetActorToken] cache size is 0
Information:[TokenCache:GetActorToken] try to get a new token synchronously
Information:[ACSTokenBuildRequest:BuildToken] started
Information:[TokenBuildRequest:GetActorTokenFromAuthServer] Sending token request to ‘https://accounts.accesscontrol.windows.net/tokens/OAuth/2’ for the resource
‘00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8’ with token: grant_type=http%3a%2f%2foauth.net%2fgrant_type%2fjwt%2f1.0%2fbearer&assertion=eyJhbGciOiJSUzI1NiIsImtpZCI
6IjkzMUU5MjNBMDVEODI5Nzk3ODBGNDAxM0I0M0E4QTc0REQ0QTUxRDEiLCJ0eXAiOiJKV1QiLCJ4NWMiOiJNSUlHNERDQ0JjaWdBd0lCQWdJVGZ3Q01lVjNwd3ZBVy9tWXArZ0FDQUl4NVhUQU5CZ2txaGtpRzl3MEJBUXNGQURCRU1STXdFUVlLQ1pJbWlaUHlMR1FCR1JZRFIwSk1NUk13RVFZS
0NaSW1pWlB5TEdRQkdSWURRVTFGTVJnd0ZnWURWUVFERXc5QlRVVWdTVzVtY21FZ1EwRWdNREl3SGhjTk1qRXdNekExTURneE5ESTVXaGNOTWpJd01qSTRNRGd4TkRJNVdqQXFNU2d3SmdZRFZRUURFeDlsYzNSelkyeHBaVzUwTG1OdmNtVmhkWFJvTG05MWRHeHZiMnN1WTI5dE1JSUJJakFOQmd
rcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBMDlUWlJrNDFNU3dJWjVobEZna01jYm1KRmkycjdPVzlKZ29uTTFmYnUxUy9aNnZBMklhZXFBVURaWVpOQ21iVzdpdDhHend0VjQrVlVMQkU3QXh0ck1VMk9YU2hjWHk4Q1ZBYmNoRDc3VE9xU0xkMjM1ZVZFM1BzTnJFa3ZGcUNPNlliV
FNGK1FRWHh6Z0pwd0FDTDNJSEdjUHMyVnJZS09vRkoyNjN3bUpwWUJ1bzFKMmhZK0VVQ0ZXcU9YQnVWNmJQRFM2RHFvSzlJMi82YXJMUTNtTEkzQ0NTVk9TV2NnTmhnU1FuaUxISzcxSi9hb1ExN2FhQ0hFRWY0WFJKMEk4ZnhkU3hJcTJsdmhoODlENXBmMlVqdjBZM0VRQ1BidHdNS1VmUzc3N0h
1cE8xaU5xbVRoVk1XWm9zQ2FOMWFHcXdSWnhUcVpIRlE2OG9lU043MzJRSURBUUFCbzRJRDR6Q0NBOTh3SndZSkt3WUJCQUdDTnhVS0JCb3dHREFLQmdnckJnRUZCUWNEQVRBS0JnZ3JCZ0VGQlFjREFqQTlCZ2tyQmdFRUFZSTNGUWNFTURBdUJpWXJCZ0VFQVlJM0ZRaUdrT01OaE5XMGVJVHhpe
jZGbTkwV3pwMFNnV0NDOWZZcmcvTFJJQUlCWkFJQkNqQ0NBZG9HQ0NzR0FRVUZCd0VCQklJQnpEQ0NBY2d3WmdZSUt3WUJCUVVITUFLR1dtaDBkSEE2THk5amNtd3ViV2xqY205emIyWjBMbU52YlM5d2EybHBibVp5WVM5RFpYSjBjeTlDVERKUVMwbEpUbFJEUVRBeExrRk5SUzVIUWt4ZlFVMUZ
KVEl3U1c1bWNtRWxNakJEUVNVeU1EQXlLRElwTG1OeWREQldCZ2dyQmdFRkJRY3dBb1pLYUhSMGNEb3ZMMk55YkRFdVlXMWxMbWRpYkM5aGFXRXZRa3d5VUV0SlNVNVVRMEV3TVM1QlRVVXVSMEpNWDBGTlJTVXlNRWx1Wm5KaEpUSXdRMEVsTWpBd01pZ3lLUzVqY25Rd1ZnWUlLd1lCQlFVSE1BS
0dTbWgwZEhBNkx5OWpjbXd5TG1GdFpTNW5ZbXd2WVdsaEwwSk1NbEJMU1VsT1ZFTkJNREV1UVUxRkxrZENURjlCVFVVbE1qQkpibVp5WVNVeU1FTkJKVEl3TURJb01pa3VZM0owTUZZR0NDc0dBUVVGQnpBQ2hrcG9kSFJ3T2k4dlkzSnNNeTVoYldVdVoySnNMMkZwWVM5Q1RESlFTMGxKVGxSRFF
UQXhMa0ZOUlM1SFFreGZRVTFGSlRJd1NXNW1jbUVsTWpCRFFTVXlNREF5S0RJcExtTnlkREJXQmdnckJnRUZCUWN3QW9aS2FIUjBjRG92TDJOeWJEUXVZVzFsTG1kaWJDOWhhV0V2UWt3eVVFdEpTVTVVUTBFd01TNUJUVVV1UjBKTVgwRk5SU1V5TUVsdVpuSmhKVEl3UTBFbE1qQXdNaWd5S1M1a
mNuUXdIUVlEVlIwT0JCWUVGSVUrbm1tdHJVMWNlS0E3aGZhUnlRWDV3UytmTUE0R0ExVWREd0VCL3dRRUF3SUZvRENDQVNZR0ExVWRId1NDQVIwd2dnRVpNSUlCRmFDQ0FSR2dnZ0VOaGo5b2RIUndPaTh2WTNKc0xtMXBZM0p2YzI5bWRDNWpiMjB2Y0d0cGFXNW1jbUV2UTFKTUwwRk5SU1V5TUV
sdVpuSmhKVEl3UTBFbE1qQXdNaTVqY215R01XaDBkSEE2THk5amNtd3hMbUZ0WlM1blltd3ZZM0pzTDBGTlJTVXlNRWx1Wm5KaEpUSXdRMEVsTWpBd01pNWpjbXlHTVdoMGRIQTZMeTlqY213eUxtRnRaUzVuWW13dlkzSnNMMEZOUlNVeU1FbHVabkpoSlRJd1EwRWxNakF3TWk1amNteUdNV2gwZ
EhBNkx5OWpjbXd6TG1GdFpTNW5ZbXd2WTNKc0wwRk5SU1V5TUVsdVpuSmhKVEl3UTBFbE1qQXdNaTVqY215R01XaDBkSEE2THk5amNtdzBMbUZ0WlM1blltd3ZZM0pzTDBGTlJTVXlNRWx1Wm5KaEpUSXdRMEVsTWpBd01pNWpjbXd3SHdZRFZSMGpCQmd3Rm9BVXo0UllmbmIrZFlHTzJ6QnJma1p
lN3BLVWx6WXdIUVlEVlIwbEJCWXdGQVlJS3dZQkJRVUhBd0VHQ0NzR0FRVUZCd01DTUEwR0NTcUdTSWIzRFFFQkN3VUFBNElCQVFCbXdUZUVCT21ZdXYvMVRWZGZvN3V3cWRydXhaKzRDaU9KOUZERlFzYVJic0VjZ1k2dVpXS0xNZmxXQ2pjTGR0UXhiVEZhMHZGTFlEZ1hBS1p0WU1xZUFJL0F1O
StEeEtKOVJ4by9UVGx5MHE2YUNleGFvemVGdmVEbENJbWV0Smo0UXppaEV3Nkp5MlV5bElVT0duT2o2SlI0cEhKSGZ5NTZTUkU4d1QvSTB5NFdoRjRJbFpoYnowMEtYaUtNMEt2Qi95Tks2V2lnc28wNUVsRkhUU1BhcWtPZm1tUC9JR0hYWWhFWlRZQ2F2eWZRWmRDNDRDb1pRY0FGdmM3NGxEcGZ
mVy8wZ1hic3l3K3ZaTXkrZEpwTlpKcWJnbFNLU0prVWVkdXlpRlBhWXc3M2VSa0IvTHk5a0hPK294M0NDQ1J2VzNNYlZZTVV2U2hrUnlETCsvU0IiLCJ4NXQiOiJreDZTT2dYWUtYbDREMEFUdERxS2ROMUtVZEUifQ.eyJuYmYiOjE2MjQ4ODIwMzksImV4cCI6MTYyNDg4MjYzOSwiaXNzIjoiMD
AwMDAwMDItMDAwMC0wZmYxLWNlMDAtMDAwMDAwMDAwMDAwQDQxZGUzZDYyLWU1MjItNDU3ZC1hZjM5LWU0YTllY2YwNjRmOCIsImF1ZCI6IjAwMDAwMDAxLTAwMDAtMDAwMC1jMDAwLTAwMDAwMDAwMDAwMC9hY2NvdW50cy5hY2Nlc3Njb250cm9sLndpbmRvd3MubmV0QDQxZGUzZDYyLWU1MjIt
NDU3ZC1hZjM5LWU0YTllY2YwNjRmOCJ9.c0eViEt90t-UbubEgdRmFU1ixSrpoY0Ls5FaFikRqiSCI91mkPiocG7dQQ1ZKfnvUIUjpyrUzRTihDaVV_CAKtW_DmAt9Bkcrgr2fLYPLqlxoonaaOuUjIbUqt4lxouTCxiXeE-UEn9vsRn35vcGSPw890cQkGedOMiKRQc6hnh7FT9F4U4Bwz_QxNkLE
eDVPU3RIQgqx2qEwxnnFKu1g95Pe-COOL1oJgYpMfIAEYoLAjLTor1ZxYN3d_6pxzW_aghutRwTI11O6XPqYywMfzQl4lOIMMC9CV8_aAxGNKKrYQCKgIbcTDqX0KG7lWfwYOhUqFpsOfRmxKG2f7skzA&resource=00000002-0000-0ff1-ce00-000000000000%2fexwebservices.cloudm
enow.net%4041de3d62-e522-457d-af39-e4a9ecf064f8
Information:[TokenBuildRequest:GetActorTokenFromAuthServer] response headers was
Pragma: no-cache
Strict-Transport-Security: max-age=31536000; includeSubDomains
X-Content-Type-Options: nosniff
client-request-id: 1ab7109f-ce1d-4dd0-b36e-2f95ae35037f
x-ms-request-id: 0c5afa47-12ae-41b2-a7f3-5df28dcc9400
x-ms-ests-server: 2.1.11829.8 – WEULR1 ProdSlices
Cache-Control: no-store, no-cache
Content-Type: application/json; charset=utf-8
Expires: -1
P3P: CP= »DSP CUR OTPi IND OTRi ONL FIN »
Set-Cookie: fpc=Ahd3WaFsh7NGlCNWAWGbua4l2yrbAQAAAHaya9gOAAAA; expires=Wed, 28-Jul-2021 12:07:19 GMT; path=/; secure; HttpOnly; SameSite=None,esctx=AQABAAAAAAD–DLA3VO7QrddgJg7Wevrf_nk3Ftaq0q8-8HxaPhO8JFmgmtjSzERXYXVoCXQitT
2wf-VJ3MkoXjN7Qj5KWwQTsEzgbRkL1yuq1HqCROLqytxonH5kuNCq1a8eNSjCNQt9dYI94hQ71m9w94AaeNYkXLDO8njpA77BMz7MGZMAgMkn_6tG13PBCAyPUIow2sgAA; domain=.accounts.accesscontrol.windows.net; path=/; secure; HttpOnly;
SameSite=None,x-ms-gateway-slice=estsfd; path=/; secure; httponly,stsservicecookie=estsfd; path=/; secure; httponly
Date: Mon, 28 Jun 2021 12:07:18 GMT
Content-Length: 1433
Information:[ACSTokenBuildRequest:BuildToken] finished
Information:[OAuthTokenBuilder:GetAppToken] finish building apptoken; the token is {« typ »: »JWT », »alg »: »RS256″, »x5t »: »nOo3ZDrODXEK1jKWhXslHR_KXEg », »kid »: »nOo3ZDrODXEK1jKWhXslHR_KXEg »}. »oid »:
« »6768ea00-362c-495c-9e04-330cd89360e9″ » « iss »: « »00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »:
« »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624881739 » « exp »: « 1624968439 »
Information:[OAuthTokenBuilder.GetAppWithUserToken] nameid is allowed to be included in the claim set
Information:[OAuthTokenBuilder.GetAppWithUserToken] only nameid to be included in the claim: no
Information:[OAuthTokenBuilder.GetAppWithUserToken] building token with user context for the audience ‘00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8’
Information:[OAuthTokenBuilder.GetAppWithUserToken] claims count: 5
Information:[OAuthCredentials:Authenticate] send request to ‘https://exwebservices.cloudmenow.net/ews/Exchange.asmx’ with the bearer token: ‘{« alg »: »none », »typ »: »JWT »}. »iss »:
« »00000002-0000-0ff1-ce00-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »: « »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624882039 » « exp »:
« 1624910839 » ; actor: {« typ »: »JWT », »alg »: »RS256″, »x5t »: »nOo3ZDrODXEK1jKWhXslHR_KXEg », »kid »: »nOo3ZDrODXEK1jKWhXslHR_KXEg »}. »oid »: « »6768ea00-362c-495c-9e04-330cd89360e9″ » « iss »:
« »00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »: « »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624881739 » « exp »:
« 1624968439 » ‘
Token:{« alg »: »none », »typ »: »JWT »}. »iss »: « »00000002-0000-0ff1-ce00-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »:
« »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624882039 » « exp »: « 1624910839 » ; actor:
{« typ »: »JWT », »alg »: »RS256″, »x5t »: »nOo3ZDrODXEK1jKWhXslHR_KXEg », »kid »: »nOo3ZDrODXEK1jKWhXslHR_KXEg »}. »oid »: « »6768ea00-362c-495c-9e04-330cd89360e9″ » « iss »:
« »00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »: « »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624881739 » « exp »:
« 1624968439 »
Exchange Response Details:
HTTP response message:
Exception:
System.Net.WebException: The remote server returned an error: (401) Unauthorized.
at System.Net.HttpWebRequest.GetResponse()
at Microsoft.Exchange.Monitoring.TestOAuthConnectivityHelper.SendExchangeOAuthRequest(ADUser user, String orgDomain, Uri targetUri, String& diagnosticMessage, Boolean appOnly, Boolean useCachedToken, Boolean
reloadConfig), diagnostics: 2000005;reason= »The user specified by the user-context in the token does not exist. »;error_category= »invalid_user »
ResultType : Error
Identity : Microsoft.Exchange.Security.OAuth.ValidationResultNodeId
IsValid : True
ObjectState : New
This is the problem that I cannot resolve.
-
Invoke-RestMethod [OK]

-
Test-Federationtrust [OK]
[PS] C:\Windows\system32>Test-FederationTrust -UserIdentity jbon@cloudmenow.net -verbose
Begin process.
STEP 1 of 6: Getting ADUser information for jbon@cloudmenow.net…
RESULT: Success.
STEP 2 of 6: Getting FederationTrust object for jbon@cloudmenow.net…
RESULT: Success.
STEP 3 of 6: Validating that the FederationTrust has the same STS certificates as the actual certificates published by the STS in the federation metadata.
RESULT: Success.
STEP 4 of 6: Getting STS and Organization certificates from the federation trust object…
RESULT: Success.
Validating current configuration for FYDIBOHF25SPDLT.cloudmenow.net…
Validation successful.
STEP 5 of 6: Requesting delegation token…
RESULT: Success. Token retrieved.
STEP 6 of 6: Validating delegation token…
RESULT: Success.
Closing Test-FederationTrust…
RunspaceId : 96fa5a83-87bc-4bd8-9a6f-8fd8c3e312b8
Id : FederationTrustConfiguration
Type : Success
Message : FederationTrust object in ActiveDirectory is valid.
RunspaceId : 96fa5a83-87bc-4bd8-9a6f-8fd8c3e312b8
Id : FederationMetadata
Type : Success
Message : The federation trust contains the same certificates published by the security token service in its federation metadata.
RunspaceId : 96fa5a83-87bc-4bd8-9a6f-8fd8c3e312b8
Id : StsCertificate
Type : Success
Message : Valid certificate referenced by property TokenIssuerCertificate in the FederationTrust object.
RunspaceId : 96fa5a83-87bc-4bd8-9a6f-8fd8c3e312b8
Id : StsPreviousCertificate
Type : Success
Message : Valid certificate referenced by property TokenIssuerPrevCertificate in the FederationTrust object.
RunspaceId : 96fa5a83-87bc-4bd8-9a6f-8fd8c3e312b8
Id : OrganizationCertificate
Type : Success
Message : Valid certificate referenced by property OrgPrivCertificate in the FederationTrust object.
RunspaceId : 96fa5a83-87bc-4bd8-9a6f-8fd8c3e312b8
Id : TokenRequest
Type : Success
Message : Request for delegation token succeeded.
RunspaceId : 96fa5a83-87bc-4bd8-9a6f-8fd8c3e312b8
Id : TokenValidation
Type : Success
Message : Requested delegation token is valid.
-
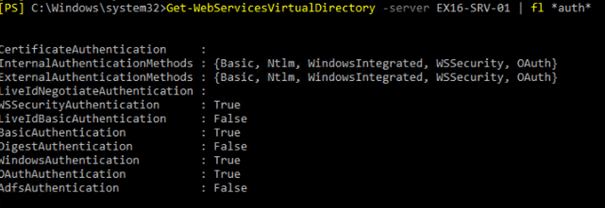
Get-WebserviceVirtualDirectory -server EX1-SRv-01 | fl *auth* [OK]
-
Get-authserver [OK]
-
Microsoft ACS
[PS] C:\Windows\system32>Get-AuthServer | fl
RunspaceId : 6ee88102-fba1-49ec-a818-8c13e1fd356d
IssuerIdentifier : 00000001-0000-0000-c000-000000000000
CertificateStrings : {MIIC8TCCAdmgAwIBAgIQQrXPXIlUE4JMTMkVj+02YTANBgkqhkiG9w0BAQsFADAjMSEwHwYDVQQDExhsb2dpbi5taWNyb3NvZnRvbmxpbmUudXMwHhcNMjEwMzEwMDAwMDAwWhcNMjYwMzEwMDAwMDAwWjAjMSEwHwYDVQQDExhsb2dpbi5taWNyb3NvZnRvbmxpbmUudX
MwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDTWt71rYFRO0210XMs0j5AQdbxeEOIMwNsYyTEdEhhcfjXMFxyxfAf28yLQe7Fcelc7PC1RgrCX3dlHfu2nqWm/CVTUd482Zmkn0P5cC9TvfHTdgqhkR1oUHf1WxXIuKHd+4+/oM8TapP5M0Tdflh0hY4YWtwyR
xcuyM74EKripxJ0EfaUGARBS4Pqeqt4tmyD6A/NIOGNVJwhRkaIPwzawrEAOIgejkqVpkjK7fa3wmRq8/2Mzsi1ICPOKDVbbK9VDNRBkD7FmomjaPEHeD9/KB09QcrpQ379yqSt/Gfb5VYfXAyGWb3RKnFMwPgehg5WLPWCAfwYJfZoGJfk7NDpAgMBAAGjITAfMB0GA1Ud
DgQWBBTECjBRANDPLGrn1p7qtwswtBU7JzANBgkqhkiG9w0BAQsFAAOCAQEAq1Ib4ERvXG5kiVmhfLOpun2ElVOLY+XkvVlyVjq35rZmSIGxgfFc08QOQFVmrWQYrlss0LbboH0cIKiD6+rVoZTMWxGEicOcGNFzrkcG0ulu0cghKYID3GKDTftYKEPkvu2vQmueqa4t2tT
3PlYF7Fi2dboR5Y96Ugs8zqNwdBMRm677N/tJBk53CsOf9NnBaxZ1EGArmEHHIb80vODStv35ueLrfMRtCF/HcgkGxy2U8kaCzYmmzHh4zYDkeCwM3Cq2bGkG+Efe9hFYfDHw13DzTR+h9pPqFFiAxnZ3ofT96NrZHdYjwbfmM8cw3ldg0xQzGcwZjtyYmwJ6sDdRvQ==,
v2ga5JsXlcOJ3gP/lE5WC1S0rjfabzdMOGP8qZQhXk4wBOgtFBaisDnbjV5pcIrjRPlhoCxvKgC/290nZ9/DLBH3TbHk8xwHXeBAnAjyAqOZij92uksAv7ZLq4MODcn
QshVINXwsYshG1pQqOLwMertNaY5WtrubMRku44Dw7R}
RsaKeyModulusExponents : <RsaKeyModulusExponentArray><RsaKeyModulusExponents /></RsaKeyModulusExponentArray>
CurrentEncryptedAppSecret :
PreviousEncryptedAppSecret :
TokenIssuingEndpoint : https://accounts.accesscontrol.windows.net/41de3d62-e522-457d-af39-e4a9ecf064f8/tokens/OAuth/2
AuthorizationEndpoint :
ApplicationIdentifier :
AuthMetadataUrl : https://accounts.accesscontrol.windows.net/41de3d62-e522-457d-af39-e4a9ecf064f8/metadata/json/1
DomainName : {cloudmenow.mail.onmicrosoft.com, cloudmenow.net, cloudmelater.online}
Realm : 41de3d62-e522-457d-af39-e4a9ecf064f8
Type : MicrosoftACS
Enabled : True
IsDefaultAuthorizationEndpoint : False
AdminDisplayName :
ExchangeVersion : 0.20 (15.0.0.0)
Name : ACS – 424d73fb-860e-45c4-a7fc-f08db2cc1de4
DistinguishedName : CN=ACS – 424d73fb-860e-45c4-a7fc-f08db2cc1de4,CN=Auth Servers,CN=Auth Configuration,CN=First Organization,CN=Microsoft Exchange,CN=Services,CN=Configuration,DC=lt01,DC=Loc
Identity : ACS – 424d73fb-860e-45c4-a7fc-f08db2cc1de4
Guid : c4e1a855-3717-4ac8-8cd1-7a3638a0d232
ObjectCategory : lt01.Loc/Configuration/Schema/ms-Exch-Auth-Auth-Server
ObjectClass : {top, msExchAuthAuthServer}
WhenChanged : 6/25/2021 8:13:25 AM
WhenCreated : 6/7/2021 12:51:29 AM
WhenChangedUTC : 6/25/2021 3:13:25 PM
WhenCreatedUTC : 6/7/2021 7:51:29 AM
OrganizationId :
Id : ACS – 424d73fb-860e-45c4-a7fc-f08db2cc1de4
OriginatingServer : WIN2K16-DC1-01.lt01.Loc
IsValid : True
ObjectState : Unchanged
-
EVOSTS
RunspaceId : 6ee88102-fba1-49ec-a818-8c13e1fd356d
IssuerIdentifier : https://sts.windows.net/41de3d62-e522-457d-af39-e4a9ecf064f8/
CertificateStrings : {MIIC8TCCAdmgAwIBAgIQQrXPXIlUE4JMTMkVj+02YTANBgkqhkiG9w0BAQsFADAjMSEwHwYDVQQDExhsb2dpbi5taWNyb3NvZnRvbmxpbmUudXMwHhcNMjEwMzEwMDAwMDAwWhcNMjYwMzEwMDAwMDAwWjAjMSEwHwYDVQQDExhsb2dpbi5taWNyb3NvZnRvbmxpbmUudX
MwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDTWt71rYFRO0210XMs0j5AQdbxeEOIMwNsYyTEdEhhcfjXMFxyxfAf28yLQe7Fcelc7PC1RgrCX3dlHfu2nqWm/CVTUd482Zmkn0P5cC9TvfHTdgqhkR1oUHf1WxXIuKHd+4+/oM8TapP5M0Tdflh0hY4YWtwyR
xcuyM74EKripxJ0EfaUGARBS4Pqeqt4tmyD6A/NIOGNVJwhRkaIPwzawrEAOIgejkqVpkjK7fa3wmRq8/2Mzsi1ICPOKDVbbK9VDNRBkD7FmomjaPEHeD9/KB09QcrpQ379yqSt/Gfb5VYfXAyGWb3RKnFMwPgehg5WLPWCAfwYJfZoGJfk7NDpAgMBAAGjITAfMB0GA1Ud
DgQWBBTECjBRANDPLGrn1p7qtwswtBU7JzANBgkqhkiG9w0BAQsFAAOCAQEAq1Ib4ERvXG5kiVmhfLOpun2ElVOLY+XkvVlyVjq35rZmSIGxgfFc08QOQFVmrWQYrlss0LbboH0cIKiD6+rVoZTMWxGEicOcGNFzrkcG0ulu0cghKYID3GKDTftYKEPkvu2vQmueqa4t2tT
3PlYF7Fi2dboR5Y96Ugs8zqNwdBMRm677N/tJBk53CsOf9NnBaxZ1EGArmEHHIb80vODStv35ueLrfMRtCF/HcgkGxy2U8kaCzYmmzHh4zYDkeCwM3Cq2bGkG+Efe9hFYfDHw13DzTR+h9pPqFFiAxnZ3ofT96NrZHdYjwbfmM8cw3ldg0xQzGcwZjtyYmwJ6sDdRvQ==,
MIIC8TCCAdmgAwIBAgIQYVk/tJ1e4phISvVrAALNKTANBgkqhkiG9w0BAQsFADAjMSEwHwYDVQQDExhsb2dpbi5taWNyb3NvZnRvbmxpbmUudXMwHhcNMjAxMjIxMDAwMDAwWhcNMjUxMjIxMDAwMDAwWjAjMSEwHwYDVQQDExhsb2dpbi5taWNyb3NvZnRvbmxpbmUudXM
wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDWfv6dZIt65ZDMFGVhJtLxGO9a+RB4PtAv185ZoZdtbvdU0YfRiKlmKw8KUW/obPB9YQJNZCnX1YV7+UBKRrn4oRaRBXMJsQxppp84izuELrU/lwaDDt2G5bizt/plgZkTNDgXmscT5g1Fu8PnWqKs83MoeTeeOL
XCuHRi1s88h/741sj3xsLAsuH1q9506aoRLNY4YQIQxe/wtIz4H1IqD/hC4G3IHDAhqRO6qjzizBMEznDw92GlZlkO0+AfztbP79aNa+T30CNeXuXylY9AmIo26O39yTc0MWnNosSmmh2FSwgPSm1EDTTx4JTqXxP67HX3BmZv/IGcdxXekVaFAgMBAAGjITAfMB0GA1UdD
gQWBBQ2r//lgTPcKughDkzmCtRlw+P9SzANBgkqhkiG9w0BAQsFAAOCAQEAsFdRyczNWh/qpYvcIZbDvWYzlrmFZc6blcUzns9zf7sUWtQZrZPu5DbetV2Gr2r3qtMDKXCUaR+pqoy3I2zxTX3x8bTNhZD9YAgAFlTLNSydTaK5RHyB/5kr6B7ZJeNIk3PRVhRGt6ybCJSj
V/VYVkLR5fdLP+5GhvBESobAR/d0ntriTzp7/tLMb/oXx7w5Hu1m3I8rpMocoXfH2SH1GLmMXj6Mx1dtwCDYM6bsb3fhWRz9O9OMR6QNiTnq8q9wn1QzBAnRcswYzT1LKKBPNFSasCvLYOCPOZCL+W8N8jqa9ZRYNYKWXzmiSptgBEM24t3m5FUWzWqoLu9pIcnkPQ==, M
IIDBTCCAe2gAwIBAgIQWPB1ofOpA7FFlOBk5iPaNTANBgkqhkiG9w0BAQsFADAtMSswKQYDVQQDEyJhY2NvdW50cy5hY2Nlc3Njb250cm9sLndpbmRvd3MubmV0MB4XDTIxMDIwNzE3MDAzOVoXDTI2MDIwNjE3MDAzOVowLTErMCkGA1UEAxMiYWNjb3VudHMuYWNjZXNz
Y29udHJvbC53aW5kb3dzLm5ldDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBALH7FzF1rjvnZ4i2iBC2tz8qs/WP61n3/wFawgJxUnTx2vP/z5pG7f8qvumd7taOII0aSlp648SIfMw59WdUUtup5CnDYOcX1sUdivAj20m2PIDK6f+KWZ+7YKxJqCzJMH4GGlQ
vuDIhRKNT9oHfZgnYCCAmjXmJBtWyD052qqrkzOSn0/e9TKbjlTnTNcrIno3XDQ7xG+79vOD2GZMNopsKogWNxUdLFRu44ClKLRb4Xe00eVrANtBkv+mSJFFJS1Gxv611hpdGI2S0v1H+KvB26O7vuzGhZ/AevRemGhXQ5V5vwNEqXnVRVkBRszLKeN/+rxM436xQyVQGJM
G+sVECAwEAAaMhMB8wHQYDVR0OBBYEFLlRBSxxgmNPObCFrl+hSsbcvRkcMA0GCSqGSIb3DQEBCwUAA4IBAQB+UQFTNs6BUY3AIGkS2ZRuZgJsNEr/ZEM4aCs2domd2Oqj7+5iWsnPh5CugFnI4nd+ZLgKVHSD6acQ27we+eNY6gxfpQCY1fiN/uKOOsA0If8IbPdBEhtPe
rRgPJFXLHaYVqD8UYDo5KNCcoB4Kh8nvCWRGPUUHPRqp7AnAcVrcbiXA/bmMCnFWuNNahcaAKiJTxYlKDaDIiPN35yECYbDj0PBWJUxobrvj5I275jbikkp8QSLYnSU/v7dMDUbxSLfZ7zsTuaF2Qx+L62PsYTwLzIFX3M8EMSQ6h68TupFTi5n0M2yIXQgoRoNEDWNJZ/a
ZMY/gqT02GQGBWrh+/vJ, MIIDBTCCAe2gAwIBAgIQN33ROaIJ6bJBWDCxtmJEbjANBgkqhkiG9w0BAQsFADAtMSswKQYDVQQDEyJhY2NvdW50cy5hY2Nlc3Njb250cm9sLndpbmRvd3MubmV0MB4XDTIwMTIyMTIwNTAxN1oXDTI1MTIyMDIwNTAxN1owLTErMCkGA1UEA
xMiYWNjb3VudHMuYWNjZXNzY29udHJvbC53aW5kb3dzLm5ldDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKGiy0/YZHEo9rRn2bI27u189Sq7NKhInFz5hLCSjgUB2rmf5ETNR3RJIDiW1M51LKROsTrjkl45cxK6gcVwLuEgr3L1TgmBtr/Rt/riKyxeXbLQ
9LGBwaNVaJrSscxfdFbJa5J+qzUIFBiFoL7kE8ZtbkZJWBTxHEyEcNC52JJ8ydOhgvZYykete8AAVa2TZAbg4ECo9+6nMsaGsSBncRHJlRWVycq8Q4HV4faMEZmZ+iyCZRo2fZufXpn7sJwZ7CEBuw4qycHvUl6y153sUUFqsswnZGGjqpKSq7I7sVI9vjB199RarHaSSbD
gL2FxjmASiUY4RqxnTjVa2XVHUwUCAwEAAaMhMB8wHQYDVR0OBBYEFI5mN5ftHloEDVNoIa8sQs7kJAeTMA0GCSqGSIb3DQEBCwUAA4IBAQBnaGnojxNgnV4+TCPZ9br4ox1nRn9tzY8b5pwKTW2McJTe0yEvrHyaItK8KbmeKJOBvASf+QwHkp+F2BAXzRiTl4Z+gNFQUL
PzsQWpmKlz6fIWhc7ksgpTkMK6AaTbwWYTfmpKnQw/KJm/6rboLDWYyKFpQcStu67RZ+aRvQz68Ev2ga5JsXlcOJ3gP/lE5WC1S0rjfabzdMOGP8qZQhXk4wBOgtFBaisDnbjV5pcIrjRPlhoCxvKgC/290nZ9/DLBH3TbHk8xwHXeBAnAjyAqOZij92uksAv7ZLq4MODcn
QshVINXwsYshG1pQqOLwMertNaY5WtrubMRku44Dw7R}
RsaKeyModulusExponents : <RsaKeyModulusExponentArray><RsaKeyModulusExponents /></RsaKeyModulusExponentArray>
CurrentEncryptedAppSecret :
PreviousEncryptedAppSecret :
TokenIssuingEndpoint : https://login.windows.net/common/oauth2/token
AuthorizationEndpoint : https://login.windows.net/common/oauth2/authorize
ApplicationIdentifier :
AuthMetadataUrl : https://login.windows.net/cloudmenow.onmicrosoft.com/federationmetadata/2007-06/federationmetadata.xml
DomainName : {}
Realm : 41de3d62-e522-457d-af39-e4a9ecf064f8
Type : AzureAD
Enabled : True
IsDefaultAuthorizationEndpoint : False
AdminDisplayName :
ExchangeVersion : 0.20 (15.0.0.0)
Name : EvoSts – 424d73fb-860e-45c4-a7fc-f08db2cc1de4
DistinguishedName : CN=EvoSts – 424d73fb-860e-45c4-a7fc-f08db2cc1de4,CN=Auth Servers,CN=Auth Configuration,CN=First Organization,CN=Microsoft Exchange,CN=Services,CN=Configuration,DC=lt01,DC=Loc
Identity : EvoSts – 424d73fb-860e-45c4-a7fc-f08db2cc1de4
Guid : 7025a371-a955-49c4-86e5-283851e577dc
ObjectCategory : lt01.Loc/Configuration/Schema/ms-Exch-Auth-Auth-Server
ObjectClass : {top, msExchAuthAuthServer}
WhenChanged : 6/7/2021 12:51:29 AM
WhenCreated : 6/7/2021 12:51:29 AM
WhenChangedUTC : 6/7/2021 7:51:29 AM
WhenCreatedUTC : 6/7/2021 7:51:29 AM
OrganizationId :
Id : EvoSts – 424d73fb-860e-45c4-a7fc-f08db2cc1de4
OriginatingServer : WIN2K16-DC1-01.lt01.Loc
IsValid : True
ObjectState : Unchanged
-
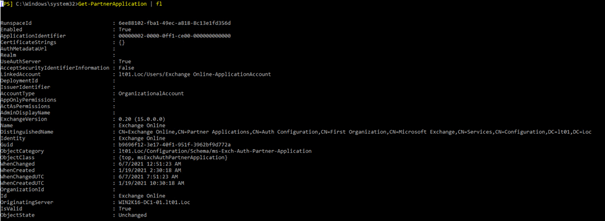
Get-partnerApplication [OK]
-
Get-ADUser -Identity jbon -properties *
AccountExpirationDate :
accountExpires : 9223372036854775807
AccountLockoutTime :
AccountNotDelegated : False
adminCount : 1
AllowReversiblePasswordEncryption : False
AuthenticationPolicy : {}
AuthenticationPolicySilo : {}
BadLogonCount : 0
badPasswordTime : 132693409367793020
badPwdCount : 0
CannotChangePassword : False
CanonicalName : lt01.Loc/Adsync/Jean Bon
Certificates : {}
City :
CN : Jean Bon
codePage : 0
Company :
CompoundIdentitySupported : {}
Country :
countryCode : 0
Created : 6/24/2021 2:31:28 AM
createTimeStamp : 6/24/2021 2:31:28 AM
Deleted :
Department :
Description :
DisplayName : Jean Bon
DistinguishedName : CN=Jean Bon,OU=Adsync,DC=lt01,DC=Loc
Division :
DoesNotRequirePreAuth : False
dSCorePropagationData : {6/24/2021 5:52:11 AM, 6/24/2021 2:31:43 AM, 12/31/1600 4:00:00 PM}
EmailAddress : jbon@cloudmenow.net
EmployeeID :
EmployeeNumber :
Enabled : True
Fax :
GivenName : Jean
HomeDirectory :
HomedirRequired : False
HomeDrive :
homeMDB : CN=Mailbox Database 0469707868,CN=Databases,CN=Exchange Administrative Group (FYDIBOHF23SPDLT),CN=Administrative Groups,CN=First Organization,CN=Microsoft
Exchange,CN=Services,CN=Configuration,DC=lt01,DC=Loc
HomePage :
HomePhone :
Initials :
instanceType : 4
isDeleted :
KerberosEncryptionType : {}
LastBadPasswordAttempt : 6/28/2021 1:02:16 AM
LastKnownParent :
lastLogoff : 0
lastLogon : 132693409471854815
LastLogonDate : 6/24/2021 2:41:27 AM
lastLogonTimestamp : 132690012872263554
legacyExchangeDN : /o=First Organization/ou=Exchange Administrative Group (FYDIBOHF23SPDLT)/cn=Recipients/cn=0ef04deb1c4c413796590fb415143682-Jean
LockedOut : False
lockoutTime : 0
logonCount : 19
LogonWorkstations :
mail : jbon@cloudmenow.net
mailNickname : jbon
Manager :
mDBUseDefaults : True
MemberOf : {CN=Domain Admins,CN=Users,DC=lt01,DC=Loc, CN=Remote Desktop Users,CN=Builtin,DC=lt01,DC=Loc}
MNSLogonAccount : False
MobilePhone :
Modified : 6/28/2021 5:20:37 AM
modifyTimeStamp : 6/28/2021 5:20:37 AM
mS-DS-ConsistencyGuid : {97, 95, 233, 100…}
msDS-ExternalDirectoryObjectId : User_6d10553b-0bf2-492c-96f4-c53a60f3eddf
msDS-User-Account-Control-Computed : 0
msExchArchiveQuota : 104857600
msExchArchiveWarnQuota : 94371840
msExchCalendarLoggingQuota : 6291456
msExchDumpsterQuota : 31457280
msExchDumpsterWarningQuota : 20971520
msExchELCMailboxFlags : 130
msExchEwsEnabled : 1
msExchEwsWellKnownApplicationPolicies : {Allow:Outlook}
msExchHomeServerName : /o=First Organization/ou=Exchange Administrative Group (FYDIBOHF23SPDLT)/cn=Configuration/cn=Servers/cn=EX16-SRV-01
msExchMailboxGuid : {91, 91, 82, 188…}
msExchMailboxSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
msExchPoliciesIncluded : {879d1743-4986-490f-947a-82afa2a09728, {26491cfc-9e50-4857-861b-0cb8df22b5d7}}
msExchRBACPolicyLink : CN=Default Role Assignment Policy,CN=Policies,CN=RBAC,CN=First Organization,CN=Microsoft Exchange,CN=Services,CN=Configuration,DC=lt01,DC=Loc
msExchRecipientDisplayType : 1073741824
msExchRecipientTypeDetails : 1
msExchTextMessagingState : {302120705, 16842751}
msExchUMDtmfMap : {emailAddress:5266, lastNameFirstName:2665326, firstNameLastName:5326266}
msExchUserAccountControl : 0
msExchUserCulture : en-US
msExchVersion : 88218628259840
msExchWhenMailboxCreated : 6/24/2021 2:32:42 AM
Name : Jean Bon
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory : CN=Person,CN=Schema,CN=Configuration,DC=lt01,DC=Loc
ObjectClass : user
ObjectGUID : 64e95f61-b315-44e3-83fd-4da0f5a29a40
objectSid : S-1-5-21-1038480083-3023236116-986656425-2603
Office :
OfficePhone :
Organization :
OtherName :
PasswordExpired : False
PasswordLastSet : 6/25/2021 7:43:33 AM
PasswordNeverExpires : True
PasswordNotRequired : False
POBox :
PostalCode :
PrimaryGroup : CN=Domain Users,CN=Users,DC=lt01,DC=Loc
primaryGroupID : 513
PrincipalsAllowedToDelegateToAccount : {}
ProfilePath :
ProtectedFromAccidentalDeletion : False
proxyAddresses : {x500:/o=ExchangeLabs/ou=Exchange Administrative Group (FYDIBOHF23SPDLT)/cn=Recipients/cn=6b1c479b974b4ca58ebfabc4d2ed11f6-jbon, smtp:jbon@cloudmenow.mail.onmicrosoft.com,
SMTP:jbon@cloudmenow.net}
pwdLastSet : 132691058135187292
SamAccountName : jbon
sAMAccountType : 805306368
ScriptPath :
sDRightsEffective : 15
ServicePrincipalNames : {}
showInAddressBook : {CN=Mailboxes(VLV),CN=All System Address Lists,CN=Address Lists Container,CN=First Organization,CN=Microsoft Exchange,CN=Services,CN=Configuration,DC=lt01,DC=Loc, CN=All Mailboxes(VLV),CN=All
System Address Lists,CN=Address Lists Container,CN=First Organization,CN=Microsoft Exchange,CN=Services,CN=Configuration,DC=lt01,DC=Loc, CN=All Recipients(VLV),CN=All System Address
Lists,CN=Address Lists Container,CN=First Organization,CN=Microsoft Exchange,CN=Services,CN=Configuration,DC=lt01,DC=Loc, CN=Default Global Address List,CN=All Global Address Lists,CN=Address
Lists Container,CN=First Organization,CN=Microsoft Exchange,CN=Services,CN=Configuration,DC=lt01,DC=Loc…}
SID : S-1-5-21-1038480083-3023236116-986656425-2603
SIDHistory : {}
SmartcardLogonRequired : False
sn : Bon
State :
StreetAddress :
Surname : Bon
Title :
TrustedForDelegation : False
TrustedToAuthForDelegation : False
UseDESKeyOnly : False
userAccountControl : 66048
userCertificate : {}
UserPrincipalName : jbon@cloudmenow.net
uSNChanged : 3539745
uSNCreated : 3485170
whenChanged : 6/28/2021 5:20:37 AM
whenCreated : 6/24/2021 2:31:28 AM
-
Set-Virtual directory Configuration
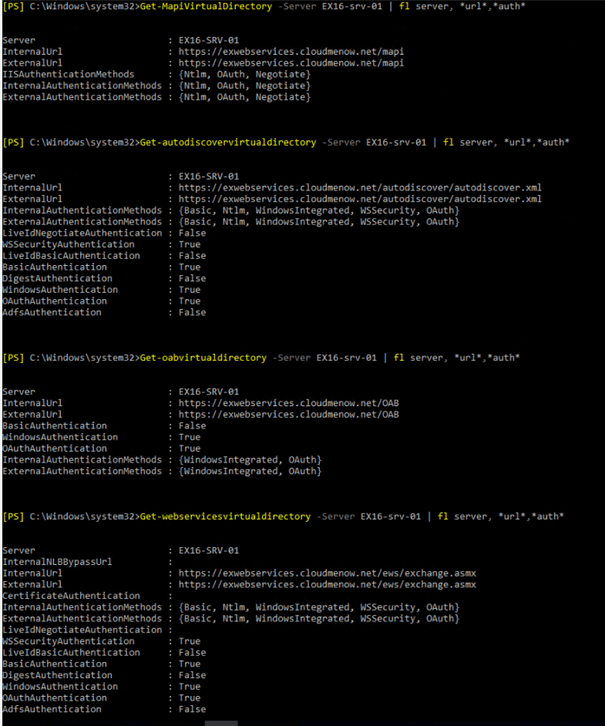
-
Online configuration
-
Get-OrganizationConfig | Select-Object Ews*
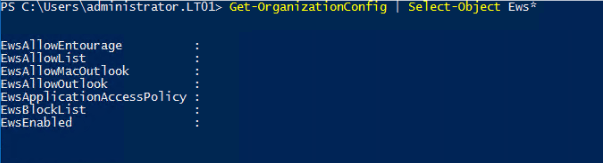
-
Teams calendar APP enabled
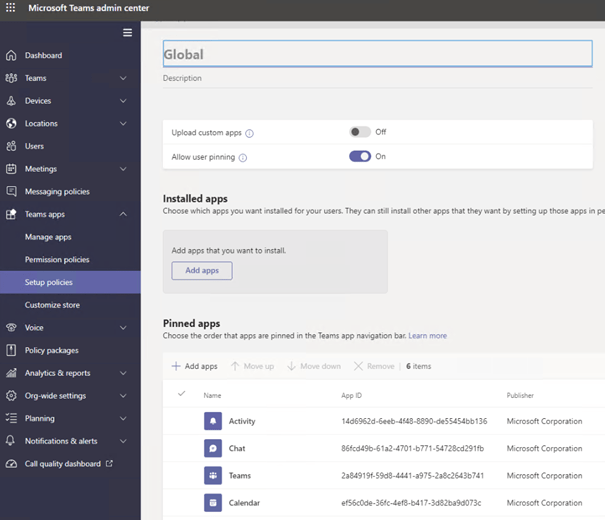
-
Get-Sharingpolicy
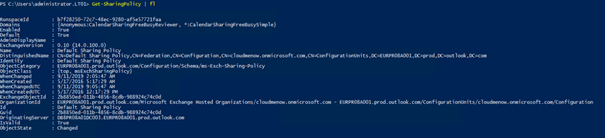
-
Get-federation Information
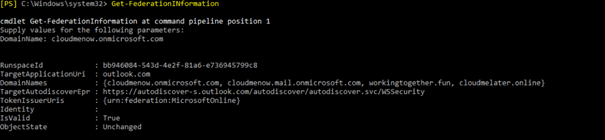
-
Get-OrganizationRelationship
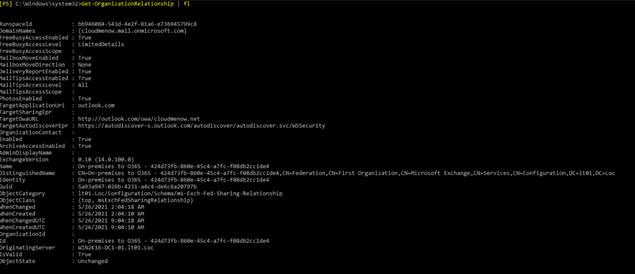
The TargetApplicationUri and TargetAutodiscoverEpr values match the equivalent values from the Get-FederationInformation cmdlet.
-
Get-mailuser -identity « jean Bon »
PS C:\Users\administrator.LT01> Get-MailUser -Identity « Jean Bon » | fl
RunspaceId : b7f28250-72c7-48ec-9280-af5e57721faa
DeliverToMailboxAndForward : False
ExchangeGuid : bc525b5b-9b34-4a0d-955e-7d9b1151893b
MailboxContainerGuid :
AggregatedMailboxGuids : {}
ArchiveGuid : 00000000-0000-0000-0000-000000000000
ArchiveName : {}
ArchiveQuota : Unlimited
ArchiveWarningQuota : Unlimited
ProhibitSendQuota : 99 GB (106,300,440,576 bytes)
ProhibitSendReceiveQuota : 100 GB (107,374,182,400 bytes)
IssueWarningQuota : 98 GB (105,226,698,752 bytes)
ForwardingAddress :
ArchiveDatabase :
ArchiveStatus : None
DisabledArchiveDatabase :
DisabledArchiveGuid : 00000000-0000-0000-0000-000000000000
MailboxProvisioningConstraint :
MailboxRegion :
MailboxRegionSuffix : None
MailboxRegionLastUpdateTime :
MailboxProvisioningPreferences : {}
ExchangeUserAccountControl : None
ExternalEmailAddress : SMTP:jbon@cloudmenow.net
UsePreferMessageFormat : False
JournalArchiveAddress :
MessageFormat : Mime
MessageBodyFormat : TextAndHtml
MacAttachmentFormat : BinHex
ProtocolSettings : {}
RecipientLimits : Unlimited
SamAccountName : $GO3E71-K7O9ME0J7PNF
UseMapiRichTextFormat : UseDefaultSettings
UserPrincipalName : jbon@cloudmenow.net
WindowsLiveID : jbon@cloudmenow.net
MicrosoftOnlineServicesID : jbon@cloudmenow.net
MailboxMoveTargetMDB :
MailboxMoveSourceMDB :
MailboxMoveFlags : None
MailboxMoveRemoteHostName :
MailboxMoveBatchName :
MailboxMoveStatus : None
MailboxRelease :
ArchiveRelease :
ImmutableId :
PersistedCapabilities : {}
SKUAssigned :
ResetPasswordOnNextLogon : False
WhenMailboxCreated :
LitigationHoldEnabled : False
SingleItemRecoveryEnabled : False
ComplianceTagHoldApplied : False
WasInactiveMailbox : False
DelayHoldApplied : False
DelayReleaseHoldApplied : False
InactiveMailboxRetireTime :
OrphanSoftDeleteTrackingTime :
RetentionHoldEnabled : False
EndDateForRetentionHold :
StartDateForRetentionHold :
RetentionComment :
RetentionUrl :
LitigationHoldDate :
LitigationHoldOwner :
RetainDeletedItemsFor : 14.00:00:00
CalendarVersionStoreDisabled : False
UsageLocation : France
SharedWithReference :
JoinedSmtpAddress :
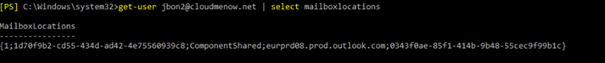
MailboxLocations : {1;832db1bd-bcf7-49cf-985b-db7e0ea735e7;ComponentShared;eurprd08.prod.outlook.com;f9dd1e3a-1f0c-47c3-a8ca-afc33ecb790b}
IsSoftDeletedByRemove : False
IsSoftDeletedByDisable : False
IsInactiveMailbox : False
WhenSoftDeleted :
InPlaceHolds : {}
RecoverableItemsQuota : 100 GB (107,374,182,400 bytes)
RecoverableItemsWarningQuota : 98 GB (105,226,698,752 bytes)
UserCertificate : {}
UserSMimeCertificate : {}
AccountDisabled : False
StsRefreshTokensValidFrom : 6/24/2021 2:35:21 AM
DataEncryptionPolicy :
OtherMail :
GuestInfo :
Extensions : {}
HasPicture : False
HasSpokenName : False
IsDirSynced : True
AcceptMessagesOnlyFrom : {}
AcceptMessagesOnlyFromDLMembers : {}
AcceptMessagesOnlyFromSendersOrMembers : {}
AddressListMembership : {\All Mail Users(VLV), \All Recipients(VLV), \Offline Global Address List, \All Users…}
AdministrativeUnits : {}
Alias : jbon
ArbitrationMailbox :
BypassModerationFromSendersOrMembers : {}
OrganizationalUnit : eurpr08a001.prod.outlook.com/Microsoft Exchange Hosted Organizations/cloudmenow.onmicrosoft.com
CustomAttribute1 :
CustomAttribute10 :
CustomAttribute11 :
CustomAttribute12 :
CustomAttribute13 :
CustomAttribute14 :
CustomAttribute15 :
CustomAttribute2 :
CustomAttribute3 :
CustomAttribute4 :
CustomAttribute5 :
CustomAttribute6 :
CustomAttribute7 :
CustomAttribute8 :
CustomAttribute9 :
ExtensionCustomAttribute1 : {}
ExtensionCustomAttribute2 : {}
ExtensionCustomAttribute3 : {}
ExtensionCustomAttribute4 : {}
ExtensionCustomAttribute5 : {}
DisplayName : Jean Bon
EmailAddresses : {SIP:jbon@cloudmenow.net, smtp:jbon@cloudmenow.mail.onmicrosoft.com, smtp:jbon@cloudmenow.onmicrosoft.com, X500:/o=First Organization/ou=Exchange Administrative Group
(FYDIBOHF23SPDLT)/cn=Recipients/cn=0ef04deb1c4c413796590fb415143682-Jean…}
GrantSendOnBehalfTo : {}
ExternalDirectoryObjectId : 6d10553b-0bf2-492c-96f4-c53a60f3eddf
HiddenFromAddressListsEnabled : False
LastExchangeChangedTime :
LegacyExchangeDN : /o=ExchangeLabs/ou=Exchange Administrative Group (FYDIBOHF23SPDLT)/cn=Recipients/cn=6b1c479b974b4ca58ebfabc4d2ed11f6-jbon
MaxSendSize : Unlimited
MaxReceiveSize : Unlimited
ModeratedBy : {}
ModerationEnabled : False
PoliciesIncluded : {}
PoliciesExcluded : {{26491cfc-9e50-4857-861b-0cb8df22b5d7}}
EmailAddressPolicyEnabled : False
PrimarySmtpAddress : jbon@cloudmenow.net
RecipientType : MailUser
RecipientTypeDetails : MailUser
RejectMessagesFrom : {}
RejectMessagesFromDLMembers : {}
RejectMessagesFromSendersOrMembers : {}
RequireSenderAuthenticationEnabled : False
SimpleDisplayName :
SendModerationNotifications : Always
UMDtmfMap : {emailAddress:5266, lastNameFirstName:2665326, firstNameLastName:5326266}
WindowsEmailAddress : jbon@cloudmenow.net
MailTip :
MailTipTranslations : {}
Identity : Jean Bon
Id : Jean Bon
IsValid : True
ExchangeVersion : 1.1 (15.0.0.0)
Name : Jean Bon
DistinguishedName : CN=Jean Bon,OU=cloudmenow.onmicrosoft.com,OU=Microsoft Exchange Hosted Organizations,DC=EURPR08A001,DC=prod,DC=outlook,DC=com
ObjectCategory : EURPR08A001.prod.outlook.com/Configuration/Schema/Person
ObjectClass : {top, person, organizationalPerson, user}
WhenChanged : 6/24/2021 3:23:35 AM
WhenCreated : 6/24/2021 2:35:55 AM
WhenChangedUTC : 6/24/2021 10:23:35 AM
WhenCreatedUTC : 6/24/2021 9:35:55 AM
ExchangeObjectId : 669270d5-4da0-41e9-a57a-5763c4d1abdf
OrganizationId : EURPR08A001.prod.outlook.com/Microsoft Exchange Hosted Organizations/cloudmenow.onmicrosoft.com – EURPR08A001.prod.outlook.com/ConfigurationUnits/cloudmenow.onmicrosoft.com/Configuration
Guid : 669270d5-4da0-41e9-a57a-5763c4d1abdf
OriginatingServer : DB8PR08A01DC003.EURPR08A001.prod.outlook.com
ObjectState : Changed
-
Get-MsolServicePrincipal -AppPrincipalId 00000002-0000-0ff1-ce00-000000000000 | select -ExpandProperty ServicePrincipalNames
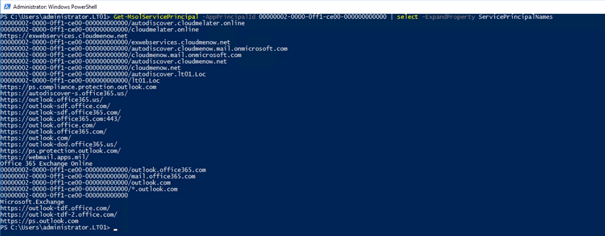
-
Autodiscover Request in IIS WSC1
In my IIS Server I can see the Autodiscover request
2021-06-25 13:31:11 10.10.10.22 POST /autodiscover/autodiscover.svc &CorrelationID=<empty>;&cafeReqId=5164f6da-87fd-4dd6-9762-690d84dfdf3d; 443 00000002-0000-0ff1-ce00-000000000000 40.101.49.141 ASAutoDiscover/CrossForest/EmailDomain//15.20.4219.029/Freebusy – 200 0 0 3075
But for the Freebusy request
ASAutoDiscover/CrossForest/EmailDomain//15.20.4219.029/Freebusy – 200 0 0 3075
2021-06-25 13:31:11 10.10.10.22 POST /ews/exchange.asmx &CorrelationID=<empty>;&cafeReqId=f0bbfe48-dd5c-40e8-87d1-d59a3d912969; 443 – 40.101.49.141 ASProxy/CrossForest/EmailDomain//15.20.4219.029/Freebusy – 401 0 0 61
2021-06-25 13:31:11 10.10.10.22 POST /ews/exchange.asmx &CorrelationID=<empty>;&cafeReqId=6c12146e-e579-4503-955c-ef6a9bf08113; 443 – 40.101.49.141 ASProxy/CrossForest/EmailDomain//15.20.4219.029/Freebusy – 401 0 0 64
2021-06-25 13:31:11 10.10.10.22 POST /ews/exchange.asmx &CorrelationID=<empty>;&cafeReqId=676cb8ff-dadb-40d9-8aba-86fd88d32069; 443 – 40.101.49.141 ASProxy/CrossForest/EmailDomain//15.20.4219.029/Freebusy – 401 0 0 107
2021-06-25 13:31:11 10.10.10.22 POST /ews/exchange.asmx &CorrelationID=<empty>;&cafeReqId=7d91a8e1-a0fc-49ea-adc9-e380f8c2ad2f; 443 – 40.101.49.141 ASProxy/CrossForest/EmailDomain//15.20.4219.029/Freebusy – 401 0 0 52
2021-06-25 13:31:11 10.10.10.22 POST /ews/exchange.asmx &CorrelationID=<empty>;&cafeReqId=bafb0853-c145-40ab-bd44-088d6d3e0a79; 443 – 40.101.49.141 ASProxy/CrossForest/EmailDomain//15.20.4219.029/Freebusy – 401 0 0 51
2021-06-25 13:31:11 10.10.10.22 POST /ews/exchange.asmx &CorrelationID=<empty>;&cafeReqId=a279b9c2-9820-47e3-8bb4-20a559dc6f59; 443 – 40.101.49.141 ASProxy/CrossForest/EmailDomain//15.20.4219.029/Freebusy – 401 0 0 249
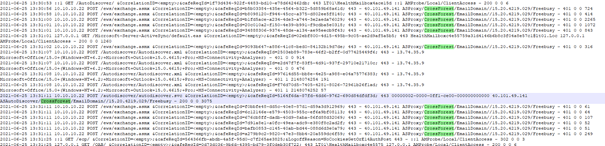
-
get-msoluser -UserPrincipalName jbon@cloudmenow.net | fl
ExtensionData : System.Runtime.Serialization.ExtensionDataObject
AlternateEmailAddresses : {}
AlternateMobilePhones : {}
AlternativeSecurityIds : {}
BlockCredential : False
City :
CloudExchangeRecipientDisplayType : -2147483642
Country :
Department :
DirSyncProvisioningErrors : {}
DisplayName : Jean Bon
Errors :
Fax :
FirstName : Jean
ImmutableId : YV/pZBWz40SD/U2g9aKaQA==
IndirectLicenseErrors : {}
IsBlackberryUser : False
IsLicensed : True
LastDirSyncTime : 6/24/2021 10:38:25 AM
LastName : Bon
LastPasswordChangeTimestamp :
LicenseAssignmentDetails : {Microsoft.Online.Administration.LicenseAssignmentDetail}
LicenseReconciliationNeeded : False
Licenses : {cloudmenow:ENTERPRISEPACK}
LiveId : 1003200156B0B79B
MSExchRecipientTypeDetails : 1
MSRtcSipDeploymentLocator :
MSRtcSipPrimaryUserAddress :
MobilePhone :
ObjectId : 6d10553b-0bf2-492c-96f4-c53a60f3eddf
Office :
OverallProvisioningStatus : Success
PasswordNeverExpires :
PasswordResetNotRequiredDuringActivate :
PhoneNumber :
PortalSettings :
PostalCode :
PreferredDataLocation :
PreferredLanguage :
ProxyAddresses : {smtp:jbon@cloudmenow.onmicrosoft.com, smtp:jbon@cloudmenow.mail.onmicrosoft.com, SMTP:jbon@cloudmenow.net}
ReleaseTrack :
ServiceInformation : {}
SignInName : jbon@cloudmenow.net
SoftDeletionTimestamp :
State :
StreetAddress :
StrongAuthenticationMethods : {}
StrongAuthenticationPhoneAppDetails : {}
StrongAuthenticationProofupTime :
StrongAuthenticationRequirements : {}
StrongAuthenticationUserDetails :
StrongPasswordRequired :
StsRefreshTokensValidFrom : 6/24/2021 9:35:21 AM
Title :
UsageLocation : FR
UserLandingPageIdentifierForO365Shell :
UserPrincipalName : jbon@cloudmenow.net
UserThemeIdentifierForO365Shell :
UserType : Member
ValidationStatus : Healthy
WhenCreated : 6/24/2021 9:35:20 AM
-
Get-CsOnlineUser -Identity jbon@cloudmenow.net | fl
RunspaceId : b0b3b18f-4b1e-44c1-8bbe-6c49691670d8
UserAccountControl : PasswordNotRequired, NormalAccount
Id : CN=6d10553b-0bf2-492c-96f4-c53a60f3eddf,OU=41de3d62-e522-457d-af39-e4a9ecf064f8,OU=OCS Tenants,DC=lync1e001,DC=local
CountryAbbreviation :
CountryOrRegionDisplayName :
Company :
Department :
Description : {}
Fax :
HomePhone :
IPPhone :
City :
Manager :
MobilePhone :
OriginatorSid :
OtherTelephone : {}
Office :
PostalCode :
PreferredLanguage :
Puid : 1003200156B0B79B
ServiceInfo : {}
StateOrProvince :
Street :
StreetAddress :
ThumbnailPhoto :
Title :
Phone :
WebPage :
AdminDescription :
AssignedPlan : {<XmlValueAssignedPlan xmlns:xsd= »http://www.w3.org/2001/XMLSchema » xmlns:xsi= »http://www.w3.org/2001/XMLSchema-instance »>
<Plan SubscribedPlanId= »8b8f6a7c-9ac7-4354-a3cd-dd1f209fa0ad » ServiceInstance= »TeamspaceAPI/NA001″ CapabilityStatus= »Enabled » AssignedTimestamp= »2021-06-24T09:35:20Z »
ServicePlanId= »57ff2da0-773e-42df-b2af-ffb7a2317929″ xmlns= »http://schemas.microsoft.com/online/directoryservices/change/2008/11″>
<Capability>
<Capability Plan= »Teams » xmlns= »http://schemas.microsoft.com/online/TeamspaceAPI/2016/09″ />
</Capability>
</Plan>
</XmlValueAssignedPlan>}
InterpretedUserType : AADConnectEnabledOnlineTeamsOnlyUser
Alias : jbon
BaseSimpleUrl :
DirSyncEnabled : True
ObjectId : 6d10553b-0bf2-492c-96f4-c53a60f3eddf
UsageLocation : FR
HideFromAddressLists : False
OnPremHideFromAddressLists : False
ProvisionedPlan : {}
ProvisioningStamp :
SubProvisioningStamp :
UpgradeRetryCounter : 0
SyncingCounter :
ProvisioningCounter : 0
SubProvisioningCounter : 0
PublishingStamp :
PublishingCounter : 0
OnPremHostingProvider :
OnPremOptionFlags : 0
OnPremEnterpriseVoiceEnabled : False
OnPremSIPEnabled :
OnPremSipAddress :
OnPremLineURI :
MCOValidationError : {}
ShadowProxyAddresses : {x500:/o=ExchangeLabs/ou=Exchange Administrative Group (FYDIBOHF23SPDLT)/cn=Recipients/cn=6b1c479b974b4ca58ebfabc4d2ed11f6-jbon, SMTP:jbon@cloudmenow.net,
smtp:jbon@cloudmenow.mail.onmicrosoft.com}
SipProxyAddress : sip:jbon@cloudmenow.net
ServiceInstance : microsoftcommunicationsonline/emea-1e-m1
StsRefreshTokensValidFrom : 6/24/2021 11:35:21 AM
LicenseRemovalTimestamp :
LastSyncTimeStamp : 6/24/2021 12:40:15 PM
LastProvisionTimeStamp : 6/24/2021 11:45:39 AM
LastPublishTimeStamp : 6/24/2021 11:48:10 AM
LastSubProvisionTimeStamp : 6/24/2021 11:47:07 AM
ExchUserHoldPolicies : {}
OwnerUrn :
ContactOptionFlags :
OnlineDialinConferencingPolicy :
OverridePreferredDataLocation :
PreferredDataLocation :
SubProvisionLineType :
UserProvisionType :
SamAccountName : $ITREV9-1PNNF5A2GETB
UserPrincipalName : jbon@cloudmenow.net
FirstName : Jean
LastName : Bon
WindowsEmailAddress : jbon@cloudmenow.net
Sid : S-1-5-21-2325497807-2625590715-1296953786-334983090
LineServerURI :
SoftDeletionTimestamp :
PendingDeletion : False
AudioVideoDisabled : False
IPPBXSoftPhoneRoutingEnabled : False
RemoteCallControlTelephonyEnabled : False
PrivateLine :
AcpInfo : {}
OriginalPreferredDataLocation :
HostedVoiceMail :
DisplayName : Jean Bon
ProxyAddresses : {x500:/o=ExchangeLabs/ou=Exchange Administrative Group (FYDIBOHF23SPDLT)/cn=Recipients/cn=6b1c479b974b4ca58ebfabc4d2ed11f6-jbon, sip:jbon@cloudmenow.net, SMTP:jbon@cloudmenow.net,
smtp:jbon@cloudmenow.mail.onmicrosoft.com…}
HomeServer :
TargetServerIfMoving :
EnterpriseVoiceEnabled : False
EnabledForRichPresence : True
ExchangeArchivingPolicy : Uninitialized
NonPrimaryResource : False
MNCReady : True
TeamsVoiceRoute : False
OnPremLineURIManuallySet : False
OptionFlags : 131328
LineURI :
SipAddress : sip:jbon@cloudmenow.net
Enabled : True
TenantId : 41de3d62-e522-457d-af39-e4a9ecf064f8
UserRoutingGroupId : a8b22dae-883f-5213-a0c3-3ee912a7747d
TargetRegistrarPool :
VoicePolicy :
CallerIdPolicy :
CallingLineIdentity :
MobilityPolicy : MobilityEnableOutsideVoice
ConferencingPolicy : BposSAllModality
BroadcastMeetingPolicy :
CloudMeetingPolicy :
CloudMeetingOpsPolicy :
TeamsMeetingPolicy :
TeamsCallingPolicy :
TeamsInteropPolicy :
TeamsMessagingPolicy :
TeamsUpgradeEffectiveMode : TeamsOnly
TeamsUpgradeNotificationsEnabled : False
TeamsUpgradePolicyIsReadOnly : ModeAndNotifications
TeamsUpgradePolicy :
TeamsCortanaPolicy :
TeamsOwnersPolicy :
TeamsMeetingBroadcastPolicy :
TeamsAppPermissionPolicy :
TeamsAppSetupPolicy :
TeamsCallParkPolicy :
TeamsEnhancedEncryptionPolicy :
TeamsEducationAssignmentsAppPolicy :
TeamsUpdateManagementPolicy :
TeamsNotificationAndFeedsPolicy :
TeamsChannelsPolicy :
TeamsSyntheticAutomatedCallPolicy :
TeamsTargetingPolicy :
TeamsVerticalPackagePolicy :
TeamsComplianceRecordingPolicy :
TeamsMobilityPolicy :
TeamsTasksPolicy :
TeamsIPPhonePolicy :
TeamsEmergencyCallRoutingPolicy :
TeamsNetworkRoamingPolicy :
TeamsCarrierEmergencyCallRoutingPolicy :
TeamsEmergencyCallingPolicy :
TeamsShiftsAppPolicy :
TeamsShiftsPolicy :
TeamsUpgradeOverridePolicy :
TeamsVideoInteropServicePolicy :
TeamsWorkLoadPolicy :
ClientUpdatePolicy :
ClientUpdateOverridePolicy :
OnlineVoicemailPolicy :
PresencePolicy :
VoiceRoutingPolicy :
RegistrarPool : sippoolDB41E07.infra.lync.com
DialPlan : FR
TenantDialPlan :
IPPhonePolicy :
LocationPolicy :
ClientPolicy :
ClientVersionPolicy :
ArchivingPolicy :
LegalInterceptPolicy :
PinPolicy :
CallViaWorkPolicy :
GraphPolicy :
ExternalAccessPolicy :
HostedVoicemailPolicy :
UserServicesPolicy :
ExperiencePolicy : W15DefaultUX
XForestMovePolicy :
PreferredDataLocationOverwritePolicy :
AddressBookPolicy :
SmsServicePolicy :
ExternalUserCommunicationPolicy :
ThirdPartyVideoSystemPolicy :
CloudVideoInteropPolicy :
ApplicationAccessPolicy :
OnlineDialOutPolicy :
OnlineVoiceRoutingPolicy :
OnlineAudioConferencingRoutingPolicy :
TeamsSurvivableBranchAppliancePolicy :
TeamsAudioConferencingPolicy :
TeamsMeetingBrandingPolicy :
TeamsVdiPolicy :
TeamsTemplatePermissionPolicy :
HostingProvider : sipfed.online.lync.com
ExUmEnabled : False
TeamsFeedbackPolicy :
TeamsCallHoldPolicy :
TeamsFilesPolicy :
Name : 6d10553b-0bf2-492c-96f4-c53a60f3eddf
DistinguishedName : CN=6d10553b-0bf2-492c-96f4-c53a60f3eddf,OU=41de3d62-e522-457d-af39-e4a9ecf064f8,OU=OCS Tenants,DC=lync1e001,DC=local
Identity : CN=6d10553b-0bf2-492c-96f4-c53a60f3eddf,OU=41de3d62-e522-457d-af39-e4a9ecf064f8,OU=OCS Tenants,DC=lync1e001,DC=local
Guid : 43973b13-6371-42d0-8154-f681ebf2e4f9
ObjectCategory : CN=Person,CN=Schema,CN=Configuration,DC=lync1e001,DC=local
ObjectClass : {top, person, organizationalPerson, user}
WhenChanged : 6/24/2021 12:40:35 PM
WhenCreated : 6/24/2021 11:42:32 AM
OriginatingServer : WE01E00ADS02.lync1e001.local
IsByPassValidation : True
IsValid : True
ObjectState : Unchanged
-
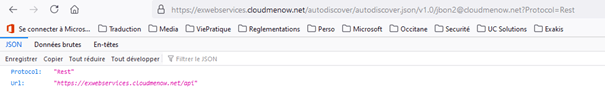
https://exwebservices.cloudmenow.net/autodiscover/autodiscover.json/v1.0/jbon2@cloudmenow.net?Protocol=Rest
-
get-user jbon2@cloudmenow.net | select mailboxlocations
-
Tests
-
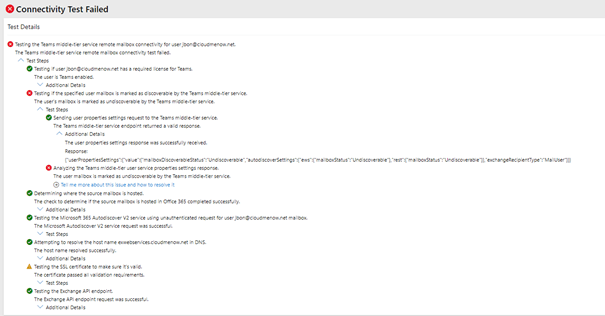
Test Calendar
-
Autodiscover Test
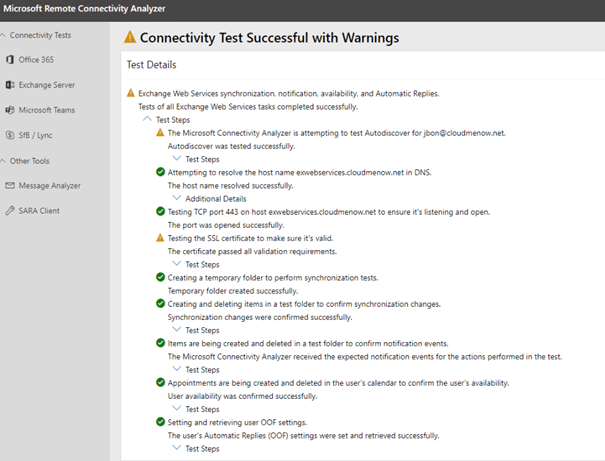
-
Free BusyTEst

-
Calendar Tab
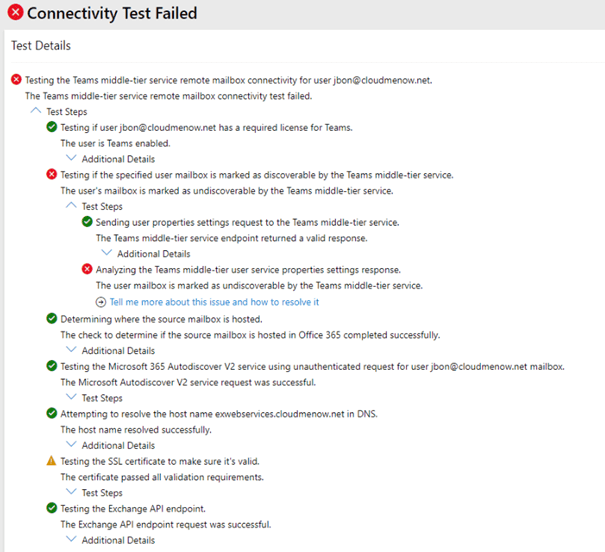
-
Free Busy Test with other EWS configuration
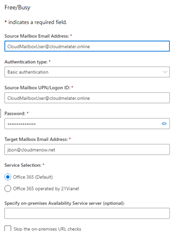
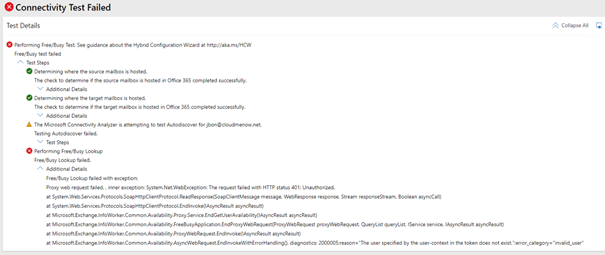
-
Analysis
This morning after having searched for two hours in the EWS logs of exchange Onprem and having found nothing I was interested in the analysis of the logs of the command
Test-OAuthConnectivity -Service EWS -TargetUri https://exwebservices.cloudmenow.net/metadata/json/1 -Mailbox CloudMailboxUser@cloudmelater.online -Verbose | Format-List
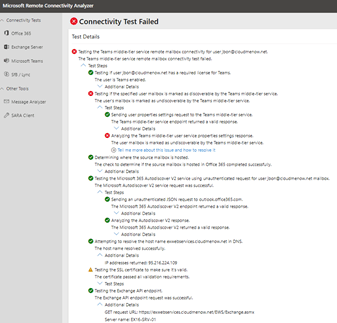
This command reproduces a freebusy request from Exchange Online to Exchange OnPrem. We know that this request is not successful because it is refused.
If we look closely at the EWS logs of the local server we can see the consequence of this error but above all we can see that the request sent from Exchange Online to the Exchange OnPrem server is not authenticated (IsAuthenticated column)

Figure 1 : EWS Log
By analyzing the logs of the Test-OAuthConnectivity command, we can observe the following
System.Net.WebException: The remote server returned an error: (401) Unauthorized.
at System.Net.HttpWebRequest.GetResponse()
at Microsoft.Exchange.Monitoring.TestOAuthConnectivityHelper.SendExchangeOAuthRequest(ADUser user, String orgDomain, Uri targetUri, String& diagnosticMessage, Boolean appOnly, Boolean useCachedToken, Boolean reloadConfig), diagnostics: 2000005;reason= »The user specified by the user-context in the token does not exist. »;error_category= »invalid_user »
.
We can see that the test tries to connect with modern auth (with Bearer Token) on the Exchange 2016 On premise services but the Exchange 2016 On prem services are not configured for modern auth. As a result the authentication fails and generates a 401 access denied.
The problem in all this is that nowhere in the Microsoft documentation is there any reference to the need to implement modern authentication on Onpremise servers.
Either the Oauth authentication set on the web services (see section Get-webservices) does not work.
The complete log of this command could be found in this section
If we do a Google search on the expression « diagnostics: 2000005;reason= »The user specified by the user context in the token does not exist. »;error_category= »invalid_user » » we find the following link: https://techcommunity.microsoft.com/t5/exchange-team-blog/announcing-hybrid-modern-authentication-for-exchange-on-premises/ba-p/607476
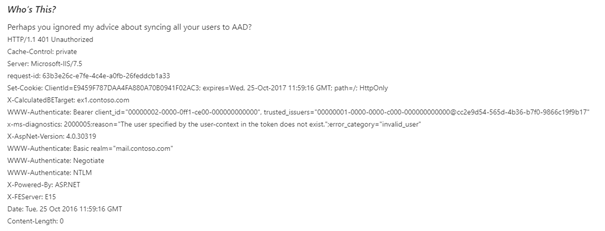
In our configuration the user is synchronized in Azure AD and represented as a mail user in Exchange online . see section mailuser
-
Actions
-
28 Jun 2021
-
Set-OrganizationConfig
When I read this article it implie that
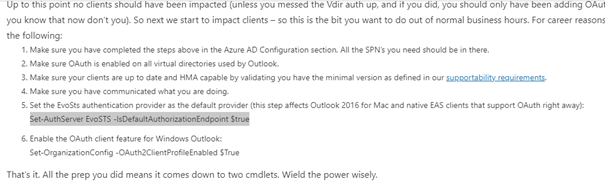
After looking at my configuration I can see that it is not the case . I decide to change that

-
Another point is « Enable the OAuth client feature for Windows Outlook:
Set-OrganizationConfig -OAuth2ClientProfileEnabled $True »
I update my config by adding this command let and try again the Free busy but still the same error on free busy test

Another point ACS authserver. I red that ACS is used for FreeBusy access and by looking the configuration i can see that
IsDefaultAuthorizationEndpoint : False
I treid to change this like the Authserver EvoSTS to $true by using this cmdlet but

-
-
Rerun the HCW
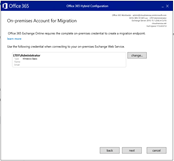
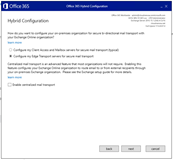
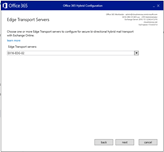
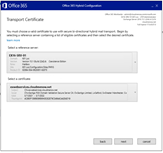
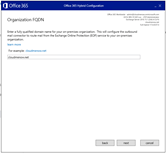
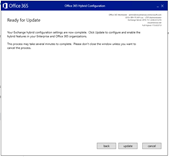
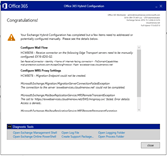
But the free busy test is still nok
-
01/07/2021
Microsoft support [Case #:26301830] call me back and ask me for a extract of the configuration Get-csuseronline -jbond@cloudmenow.net
I decided to install a new simple mockup with another tenant another local AD but without federation : Cloudmelater.online
Just to see and to check if this issue seems linked to OKTA Federation or not.
So I installed a new Exchange 2016 CU 20 server with an AD and and AD Connect. No federation but rather passwordHash.
I published everything on a web service exwebservices.cloudmelater.online and did some tests
I created two users for this
- Jbon@cloudmelater.online (Synchronized account)
- and CloudMailboxuser@cloudmelater.online (Cloud account with an E3 license)
I set the internal urls of the virtual directory so that they can all point to https://exwebservices.cloudmelater.online/…. Exactly as in the model 1 (Fed with Okta)
I made a test of Freebusy with the remote connectivity analyse from the cloud to the onpremise. I have the same error message as on the model 1 (Fed with Okta) (401). But on the other hand to my great surprise the Teams calendar Tab works !!!!!!!!

So already what we can say is that if the FreeBusy from Online to Onprem does not work it does not prevent the Teams calendar Tab to work
Tomorrow I’m going to go back to the settings of model 2 (Password Hash) and see if there are differences with the environment of model 1 (Fed With Okta). I’m going to drop this free busy thing for the moment.
-
02/07/2021
-
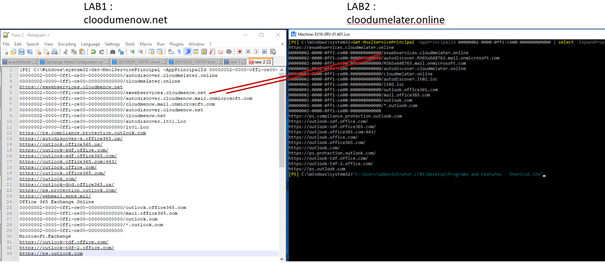
Comparing configuration
Now that I have a Lab2 that works and a Lab1 that doesn’t, I can compare the settings. Let’s go
Lab 1
Lab 2
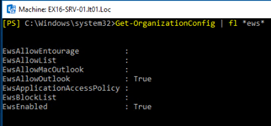
I decide to change the configuration to reflect lab2
PS] C:\Windows\system32>Set-OrganizationConfig -EwsEnabled $Null
[PS] C:\Windows\system32>Set-OrganizationConfig -EwsAllowOutlook $null
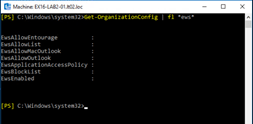
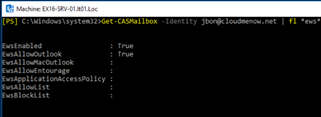
I decide to change the casmailbox settings
set-CASMailbox -Identity jbon@cloudmenow.net -EwsEnabled $null -EwsAllowOutlook $null

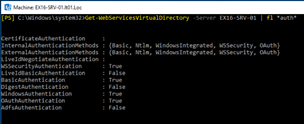
Get-WebServicesVirtualDirectory -Server EX16-SRV-01 | Set-WebServicesVirtualDirectory -BasicAut
hentication $False
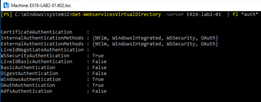
Let try if now it is working on lab1
Not this time. Same player shoot Again !: Let’s continue
Lab 1
Lab 2
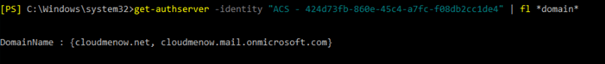
 Get-authserver
Get-authserver
Type : MicrosoftACS
DomainName : {autod:cloudmenow.net, cloudmenow.mail.onmicrosoft.com, cloudmelater.online}
*********************
Type : AzureAD
IsDefaultAuthorizationEndpoint : True
Get-authserver
Type : MicrosoftACS
DomainName : {M365x648763.mail.onmicrosoft.com, cloudmelater.online}
Type : AzureAD
IsDefaultAuthorizationEndpoint : False
I decide to change this in a lab1 as below
set-authserver -identity « ACS – 424d73fb-860e-45c4-a7fc-f08db2cc1de4 » -domainName cloudmenow.net, cloudmenow.mail.onmicrosoft.com
Let try if now it is working on lab1
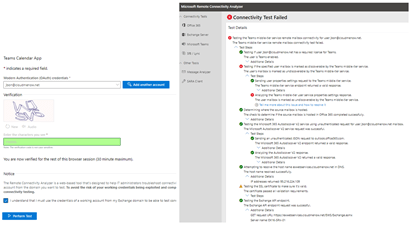
Not this time. Same player shoot Again !: Let’s continue
I decide to change in Microsoft AzureAD in lab 1 the value of IsDefaultAuthorizationEndpoint : True to False in order to reflect the Lab2 Configuration
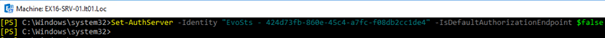
Let try if now it is working on lab1
Not this time. Same player shoot Again !: Let’s continue
-
Get-MsolServicePrincipal -AppPrincipalId 00000002-0000-0ff1-ce00-000000000000 | select -ExpandProperty ServicePrincipalNames
-
Just test with new fresh user (KO)
 Let’s try on lab1 to create a new mailboxuser .. jbon2@cloudmenow.net
Let’s try on lab1 to create a new mailboxuser .. jbon2@cloudmenow.net
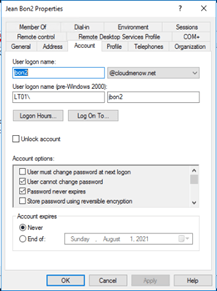
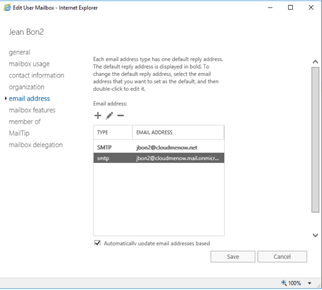
Exchange Online configuration
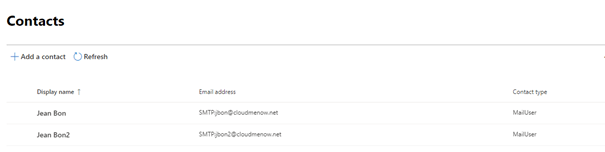
Online user information
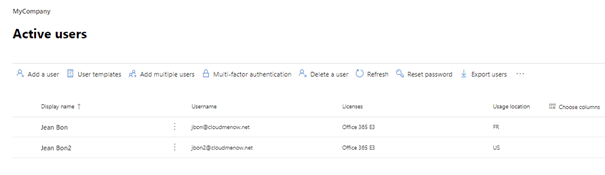
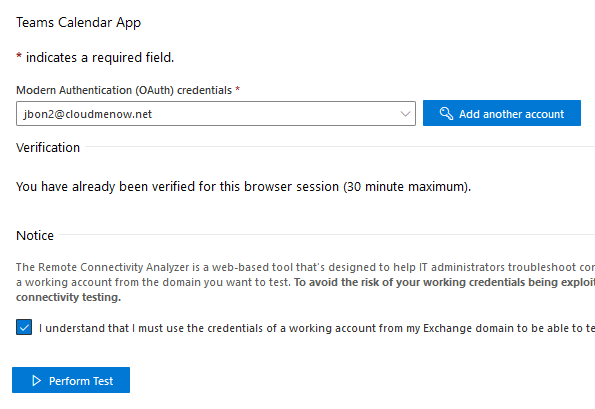
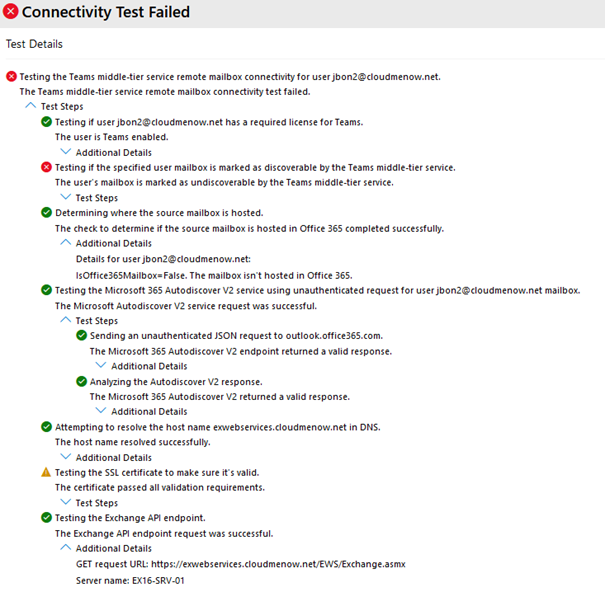
-
Teams Logs : isMailboxDiscoverable: false
In the teams log we can observe that the mailbox is not discoverable . why ? I don’t know
The test https://exwebservices.cloudmenow.net/autodiscover/autodiscover.json/v1.0/jbon2@cloudmenow.net?Protocol=Rest is good
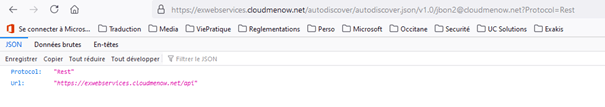
The mailbox location is good
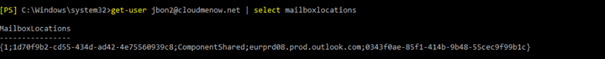
But the mailbox is still not discoverable
2021-07-02T15:25:34.803Z Inf UserAppsStore: Skipped calendar app with isFirstParty as true. isMailboxDiscoverable: false,
isFreemiumTenant: false, enableFreemiumCalendar: true
2021-07-02T15:25:34.793Z Inf UserAppsStore: Added Insights app with isFirstParty as false
2021-07-02T15:25:34.793Z Inf UserAppsStore: Added OneNote app with isFirstParty as false
2021-07-02T15:25:34.793Z Inf UserAppsStore: Added Approvals app with isFirstParty as false
2021-07-02T15:25:34.793Z Inf UserAppsStore: Added Tasks by Planner and To Do app with isFirstParty as false
2021-07-02T15:25:34.793Z Inf UserAppsStore: Added Help app with isFirstParty as false
2021-07-02T15:25:34.793Z Inf UserAppsStore: Added Wiki app with isFirstParty as false
-
Annexes
-
Log Test-OAuthConnectivity -Service EWS -TargetUri https://exwebservices.cloudmenow.net/metadata/json/1
PS C:\Users\administrator.LT01> Test-OAuthConnectivity -Service EWS -TargetUri https://exwebservices.cloudmenow.net/metadata/json/1 -Mailbox CloudMailboxUser@cloudmelater.online -Verbose | Format-List
RunspaceId : 912b6819-a6d2-44fa-8111-5a1ba0308410
Task : Checking EWS API Call Under Oauth
Detail : The configuration was last successfully loaded at 1/1/0001 12:00:00 AM UTC. This was 1062675853 minutes ago.
The token cache is being cleared because « use cached token » was set to false.
Exchange Outbound Oauth Log:
Client request ID: e7e64d23-ecd9-4f8a-80af-066da3f5d121
Information:[OAuthCredentials:Authenticate] entering
Information:[OAuthCredentials:Authenticate] challenge from ‘https://exwebservices.cloudmenow.net/ews/Exchange.asmx’ received: Bearer client_id= »00000002-0000-0ff1-ce00-000000000000″,
trusted_issuers= »00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″, token_types= »app_asserted_user_v1 service_asserted_app_v1″,Basic realm= »exwebservices.cloudmenow.net »,Negotiate,NTLM
Information:[OAuthCredentials:GetToken] client-id: ‘00000002-0000-0ff1-ce00-000000000000’, realm: », trusted_issuer: ‘00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8’
Information:[OAuthCredentials:GetToken] Start building a token using organizationId ’41de3d62-e522-457d-af39-e4a9ecf064f8′
Information:[OAuthCredentials:GetToken] Start building a token using adUser
Information:[OAuthTokenBuilder:GetAppToken] start building the apptoken
Information:[OAuthTokenBuilder:GetAppToken] checking enabled auth servers
Information:[OAuthTokenBuilder:GetAppToken] trusted_issuer includes the auth server ‘MicrosoftSts’: 00000001-0000-0000-c000-000000000000@*,
Information:[OAuthTokenBuilder:GetAppToken] trying to get the apptoken from the auth server ‘MicrosoftSts’ for resource
‘00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8′, tenantId ’41de3d62-e522-457d-af39-e4a9ecf064f8’, userDomain ‘cloudmelater.online’
Information:[TokenCache:GetActorToken] Each key and its counts are L:00000002-0000-0ff1-ce00-000000000000-AS:00000001-0000-0000-c000-000000000000@*, 0
Information:[TokenCache:GetActorToken] cache size is 0
Information:[TokenCache:GetActorToken] try to get a new token synchronously
Information:[ACSTokenBuildRequest:BuildToken] started
Information:[TokenBuildRequest:GetActorTokenFromAuthServer] Sending token request to ‘https://accounts.accesscontrol.windows.net/tokens/OAuth/2’ for the resource
‘00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8’ with token: grant_type=http%3a%2f%2foauth.net%2fgrant_type%2fjwt%2f1.0%2fbearer&assertion=eyJhbGciOiJSUzI1NiIsImtpZCI
6IjkzMUU5MjNBMDVEODI5Nzk3ODBGNDAxM0I0M0E4QTc0REQ0QTUxRDEiLCJ0eXAiOiJKV1QiLCJ4NWMiOiJNSUlHNERDQ0JjaWdBd0lCQWdJVGZ3Q01lVjNwd3ZBVy9tWXArZ0FDQUl4NVhUQU5CZ2txaGtpRzl3MEJBUXNGQURCRU1STXdFUVlLQ1pJbWlaUHlMR1FCR1JZRFIwSk1NUk13RVFZS
0NaSW1pWlB5TEdRQkdSWURRVTFGTVJnd0ZnWURWUVFERXc5QlRVVWdTVzVtY21FZ1EwRWdNREl3SGhjTk1qRXdNekExTURneE5ESTVXaGNOTWpJd01qSTRNRGd4TkRJNVdqQXFNU2d3SmdZRFZRUURFeDlsYzNSelkyeHBaVzUwTG1OdmNtVmhkWFJvTG05MWRHeHZiMnN1WTI5dE1JSUJJakFOQmd
rcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBMDlUWlJrNDFNU3dJWjVobEZna01jYm1KRmkycjdPVzlKZ29uTTFmYnUxUy9aNnZBMklhZXFBVURaWVpOQ21iVzdpdDhHend0VjQrVlVMQkU3QXh0ck1VMk9YU2hjWHk4Q1ZBYmNoRDc3VE9xU0xkMjM1ZVZFM1BzTnJFa3ZGcUNPNlliV
FNGK1FRWHh6Z0pwd0FDTDNJSEdjUHMyVnJZS09vRkoyNjN3bUpwWUJ1bzFKMmhZK0VVQ0ZXcU9YQnVWNmJQRFM2RHFvSzlJMi82YXJMUTNtTEkzQ0NTVk9TV2NnTmhnU1FuaUxISzcxSi9hb1ExN2FhQ0hFRWY0WFJKMEk4ZnhkU3hJcTJsdmhoODlENXBmMlVqdjBZM0VRQ1BidHdNS1VmUzc3N0h
1cE8xaU5xbVRoVk1XWm9zQ2FOMWFHcXdSWnhUcVpIRlE2OG9lU043MzJRSURBUUFCbzRJRDR6Q0NBOTh3SndZSkt3WUJCQUdDTnhVS0JCb3dHREFLQmdnckJnRUZCUWNEQVRBS0JnZ3JCZ0VGQlFjREFqQTlCZ2tyQmdFRUFZSTNGUWNFTURBdUJpWXJCZ0VFQVlJM0ZRaUdrT01OaE5XMGVJVHhpe
jZGbTkwV3pwMFNnV0NDOWZZcmcvTFJJQUlCWkFJQkNqQ0NBZG9HQ0NzR0FRVUZCd0VCQklJQnpEQ0NBY2d3WmdZSUt3WUJCUVVITUFLR1dtaDBkSEE2THk5amNtd3ViV2xqY205emIyWjBMbU52YlM5d2EybHBibVp5WVM5RFpYSjBjeTlDVERKUVMwbEpUbFJEUVRBeExrRk5SUzVIUWt4ZlFVMUZ
KVEl3U1c1bWNtRWxNakJEUVNVeU1EQXlLRElwTG1OeWREQldCZ2dyQmdFRkJRY3dBb1pLYUhSMGNEb3ZMMk55YkRFdVlXMWxMbWRpYkM5aGFXRXZRa3d5VUV0SlNVNVVRMEV3TVM1QlRVVXVSMEpNWDBGTlJTVXlNRWx1Wm5KaEpUSXdRMEVsTWpBd01pZ3lLUzVqY25Rd1ZnWUlLd1lCQlFVSE1BS
0dTbWgwZEhBNkx5OWpjbXd5TG1GdFpTNW5ZbXd2WVdsaEwwSk1NbEJMU1VsT1ZFTkJNREV1UVUxRkxrZENURjlCVFVVbE1qQkpibVp5WVNVeU1FTkJKVEl3TURJb01pa3VZM0owTUZZR0NDc0dBUVVGQnpBQ2hrcG9kSFJ3T2k4dlkzSnNNeTVoYldVdVoySnNMMkZwWVM5Q1RESlFTMGxKVGxSRFF
UQXhMa0ZOUlM1SFFreGZRVTFGSlRJd1NXNW1jbUVsTWpCRFFTVXlNREF5S0RJcExtTnlkREJXQmdnckJnRUZCUWN3QW9aS2FIUjBjRG92TDJOeWJEUXVZVzFsTG1kaWJDOWhhV0V2UWt3eVVFdEpTVTVVUTBFd01TNUJUVVV1UjBKTVgwRk5SU1V5TUVsdVpuSmhKVEl3UTBFbE1qQXdNaWd5S1M1a
mNuUXdIUVlEVlIwT0JCWUVGSVUrbm1tdHJVMWNlS0E3aGZhUnlRWDV3UytmTUE0R0ExVWREd0VCL3dRRUF3SUZvRENDQVNZR0ExVWRId1NDQVIwd2dnRVpNSUlCRmFDQ0FSR2dnZ0VOaGo5b2RIUndPaTh2WTNKc0xtMXBZM0p2YzI5bWRDNWpiMjB2Y0d0cGFXNW1jbUV2UTFKTUwwRk5SU1V5TUV
sdVpuSmhKVEl3UTBFbE1qQXdNaTVqY215R01XaDBkSEE2THk5amNtd3hMbUZ0WlM1blltd3ZZM0pzTDBGTlJTVXlNRWx1Wm5KaEpUSXdRMEVsTWpBd01pNWpjbXlHTVdoMGRIQTZMeTlqY213eUxtRnRaUzVuWW13dlkzSnNMMEZOUlNVeU1FbHVabkpoSlRJd1EwRWxNakF3TWk1amNteUdNV2gwZ
EhBNkx5OWpjbXd6TG1GdFpTNW5ZbXd2WTNKc0wwRk5SU1V5TUVsdVpuSmhKVEl3UTBFbE1qQXdNaTVqY215R01XaDBkSEE2THk5amNtdzBMbUZ0WlM1blltd3ZZM0pzTDBGTlJTVXlNRWx1Wm5KaEpUSXdRMEVsTWpBd01pNWpjbXd3SHdZRFZSMGpCQmd3Rm9BVXo0UllmbmIrZFlHTzJ6QnJma1p
lN3BLVWx6WXdIUVlEVlIwbEJCWXdGQVlJS3dZQkJRVUhBd0VHQ0NzR0FRVUZCd01DTUEwR0NTcUdTSWIzRFFFQkN3VUFBNElCQVFCbXdUZUVCT21ZdXYvMVRWZGZvN3V3cWRydXhaKzRDaU9KOUZERlFzYVJic0VjZ1k2dVpXS0xNZmxXQ2pjTGR0UXhiVEZhMHZGTFlEZ1hBS1p0WU1xZUFJL0F1O
StEeEtKOVJ4by9UVGx5MHE2YUNleGFvemVGdmVEbENJbWV0Smo0UXppaEV3Nkp5MlV5bElVT0duT2o2SlI0cEhKSGZ5NTZTUkU4d1QvSTB5NFdoRjRJbFpoYnowMEtYaUtNMEt2Qi95Tks2V2lnc28wNUVsRkhUU1BhcWtPZm1tUC9JR0hYWWhFWlRZQ2F2eWZRWmRDNDRDb1pRY0FGdmM3NGxEcGZ
mVy8wZ1hic3l3K3ZaTXkrZEpwTlpKcWJnbFNLU0prVWVkdXlpRlBhWXc3M2VSa0IvTHk5a0hPK294M0NDQ1J2VzNNYlZZTVV2U2hrUnlETCsvU0IiLCJ4NXQiOiJreDZTT2dYWUtYbDREMEFUdERxS2ROMUtVZEUifQ.eyJuYmYiOjE2MjQ5NTQzOTAsImV4cCI6MTYyNDk1NDk5MCwiaXNzIjoiMD
AwMDAwMDItMDAwMC0wZmYxLWNlMDAtMDAwMDAwMDAwMDAwQDQxZGUzZDYyLWU1MjItNDU3ZC1hZjM5LWU0YTllY2YwNjRmOCIsImF1ZCI6IjAwMDAwMDAxLTAwMDAtMDAwMC1jMDAwLTAwMDAwMDAwMDAwMC9hY2NvdW50cy5hY2Nlc3Njb250cm9sLndpbmRvd3MubmV0QDQxZGUzZDYyLWU1MjIt
NDU3ZC1hZjM5LWU0YTllY2YwNjRmOCJ9.Bh3oZnDknFGrCHm4dUF4w54CpmOeMZrDaKyIJH3OGpIwz1Gm8vs2pPe_k8GMfwMgztAtHkE8r6MwoLyLh3d04JYr2DewD9jsIgvOrJm97jhtxz9PhTj2Be3tArfEaoqsnEzpZpexrftJ6sn_2LAuxXQTLE15ksWMpgzNpN_QJX7zSIN5vaFvFRjOl8CpJ
fg-2Vs5TVeVFwp4VX4A1qrUhOIfxOwC66VinuTBBTuMOruDyqXpbgbJWSnRH9djuejso5_v4fucqp3F5OCby4ab95tPq4XRrFXsser1heH4ak1XWX95k0VnLeX3tuV0aB3kwB3uiqKYHXlbZo_diPLiHA&resource=00000002-0000-0ff1-ce00-000000000000%2fexwebservices.cloudm
enow.net%4041de3d62-e522-457d-af39-e4a9ecf064f8
Information:[TokenBuildRequest:GetActorTokenFromAuthServer] response headers was
Pragma: no-cache
Strict-Transport-Security: max-age=31536000; includeSubDomains
X-Content-Type-Options: nosniff
client-request-id: e7e64d23-ecd9-4f8a-80af-066da3f5d121
x-ms-request-id: 2be2af34-f374-40fe-ac03-79ca23bb7900
x-ms-ests-server: 2.1.11829.8 – NEULR2 ProdSlices
Cache-Control: no-store, no-cache
Content-Type: application/json; charset=utf-8
Expires: -1
P3P: CP= »DSP CUR OTPi IND OTRi ONL FIN »
Set-Cookie: fpc=ArvCnr7H9dhCuBChHqn4zI8l2yrbAQAAABXNbNgOAAAA; expires=Thu, 29-Jul-2021 08:13:10 GMT; path=/; secure; HttpOnly; SameSite=None,esctx=AQABAAAAAAD–DLA3VO7QrddgJg7WevrVr0ZGbDnoLLwBBbpA-DBO6L6NAQ9is8CGouHGlRscJ0
MjfDDtspRarOWbC7H6KvVC8cHv8qZJtX7v2vB0Ak7YQjRdsb81yCexNPqqxRMFwXoqrXCmdzbaQUHYF3_1i49fBzSa5SCoGqfdZaDfFjRHcRZX562HYiQlSmAcCnpFNIgAA; domain=.accounts.accesscontrol.windows.net; path=/; secure; HttpOnly;
SameSite=None,x-ms-gateway-slice=estsfd; path=/; secure; httponly,stsservicecookie=estsfd; path=/; secure; httponly
Date: Tue, 29 Jun 2021 08:13:09 GMT
Content-Length: 1433
Information:[ACSTokenBuildRequest:BuildToken] finished
Information:[OAuthTokenBuilder:GetAppToken] finish building apptoken; the token is {« typ »: »JWT », »alg »: »RS256″, »x5t »: »nOo3ZDrODXEK1jKWhXslHR_KXEg », »kid »: »nOo3ZDrODXEK1jKWhXslHR_KXEg »}. »oid »:
« »6768ea00-362c-495c-9e04-330cd89360e9″ » « iss »: « »00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »:
« »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624954090 » « exp »: « 1625040790 »
Information:[OAuthTokenBuilder.GetAppWithUserToken] nameid is allowed to be included in the claim set
Information:[OAuthTokenBuilder.GetAppWithUserToken] only nameid to be included in the claim: no
Information:[OAuthTokenBuilder.GetAppWithUserToken] building token with user context for the audience ‘00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8’
Information:[OAuthTokenBuilder.GetAppWithUserToken] claims count: 5
Information:[OAuthCredentials:Authenticate] send request to ‘https://exwebservices.cloudmenow.net/ews/Exchange.asmx’ with the bearer token: ‘{« alg »: »none », »typ »: »JWT »}. »iss »:
« »00000002-0000-0ff1-ce00-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »: « »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624954390 » « exp »:
« 1624983190 » ; actor: {« typ »: »JWT », »alg »: »RS256″, »x5t »: »nOo3ZDrODXEK1jKWhXslHR_KXEg », »kid »: »nOo3ZDrODXEK1jKWhXslHR_KXEg »}. »oid »: « »6768ea00-362c-495c-9e04-330cd89360e9″ » « iss »:
« »00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »: « »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624954090 » « exp »:
« 1625040790 » ‘
Token:{« alg »: »none », »typ »: »JWT »}. »iss »: « »00000002-0000-0ff1-ce00-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »:
« »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624954390 » « exp »: « 1624983190 » ; actor:
{« typ »: »JWT », »alg »: »RS256″, »x5t »: »nOo3ZDrODXEK1jKWhXslHR_KXEg », »kid »: »nOo3ZDrODXEK1jKWhXslHR_KXEg »}. »oid »: « »6768ea00-362c-495c-9e04-330cd89360e9″ » « iss »:
« »00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »: « »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624954090 » « exp »:
« 1625040790 »
Exchange Response Details:
HTTP response message:
Exception:
System.Net.WebException: The remote server returned an error: (401) Unauthorized.
at System.Net.HttpWebRequest.GetResponse()
at Microsoft.Exchange.Monitoring.TestOAuthConnectivityHelper.SendExchangeOAuthRequest(ADUser user, String orgDomain, Uri targetUri, String& diagnosticMessage, Boolean appOnly, Boolean useCachedToken, Boolean
reloadConfig), diagnostics: 2000005;reason= »The user specified by the user-context in the token does not exist. »;error_category= »invalid_user »
ResultType : Error
Identity : Microsoft.Exchange.Security.OAuth.ValidationResultNodeId
IsValid : True
ObjectState : New
PS C:\Users\administrator.LT01> Test-OAuthConnectivity -Service EWS -TargetUri https://exwebservices.cloudmenow.net/metadata/json/1 -Mailbox CloudMailboxUser@cloudmelater.online -Verbose | Format-List
RunspaceId : 912b6819-a6d2-44fa-8111-5a1ba0308410
Task : Checking EWS API Call Under Oauth
Detail : The configuration was last successfully loaded at 1/1/0001 12:00:00 AM UTC. This was 1062675921 minutes ago.
The token cache is being cleared because « use cached token » was set to false.
Exchange Outbound Oauth Log:
Client request ID: a54bb27e-1040-4459-8953-61d83af8d862
Information:[OAuthCredentials:Authenticate] entering
Information:[OAuthCredentials:Authenticate] challenge from ‘https://exwebservices.cloudmenow.net/ews/Exchange.asmx’ received: Bearer client_id= »00000002-0000-0ff1-ce00-000000000000″,
trusted_issuers= »00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″, token_types= »app_asserted_user_v1 service_asserted_app_v1″,Basic realm= »exwebservices.cloudmenow.net »,Negotiate,NTLM
Information:[OAuthCredentials:GetToken] client-id: ‘00000002-0000-0ff1-ce00-000000000000’, realm: », trusted_issuer: ‘00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8’
Information:[OAuthCredentials:GetToken] Start building a token using organizationId ’41de3d62-e522-457d-af39-e4a9ecf064f8′
Information:[OAuthCredentials:GetToken] Start building a token using adUser
Information:[OAuthTokenBuilder:GetAppToken] start building the apptoken
Information:[OAuthTokenBuilder:GetAppToken] checking enabled auth servers
Information:[OAuthTokenBuilder:GetAppToken] trusted_issuer includes the auth server ‘MicrosoftSts’: 00000001-0000-0000-c000-000000000000@*,
Information:[OAuthTokenBuilder:GetAppToken] trying to get the apptoken from the auth server ‘MicrosoftSts’ for resource
‘00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8′, tenantId ’41de3d62-e522-457d-af39-e4a9ecf064f8’, userDomain ‘cloudmelater.online’
Information:[TokenCache:GetActorToken] Each key and its counts are L:00000002-0000-0ff1-ce00-000000000000-AS:00000001-0000-0000-c000-000000000000@*, 0
Information:[TokenCache:GetActorToken] cache size is 0
Information:[TokenCache:GetActorToken] try to get a new token synchronously
Information:[ACSTokenBuildRequest:BuildToken] started
Information:[TokenBuildRequest:GetActorTokenFromAuthServer] Sending token request to ‘https://accounts.accesscontrol.windows.net/tokens/OAuth/2’ for the resource
‘00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8’ with token: grant_type=http%3a%2f%2foauth.net%2fgrant_type%2fjwt%2f1.0%2fbearer&assertion=eyJhbGciOiJSUzI1NiIsImtpZCI
6IjkzMUU5MjNBMDVEODI5Nzk3ODBGNDAxM0I0M0E4QTc0REQ0QTUxRDEiLCJ0eXAiOiJKV1QiLCJ4NWMiOiJNSUlHNERDQ0JjaWdBd0lCQWdJVGZ3Q01lVjNwd3ZBVy9tWXArZ0FDQUl4NVhUQU5CZ2txaGtpRzl3MEJBUXNGQURCRU1STXdFUVlLQ1pJbWlaUHlMR1FCR1JZRFIwSk1NUk13RVFZS
0NaSW1pWlB5TEdRQkdSWURRVTFGTVJnd0ZnWURWUVFERXc5QlRVVWdTVzVtY21FZ1EwRWdNREl3SGhjTk1qRXdNekExTURneE5ESTVXaGNOTWpJd01qSTRNRGd4TkRJNVdqQXFNU2d3SmdZRFZRUURFeDlsYzNSelkyeHBaVzUwTG1OdmNtVmhkWFJvTG05MWRHeHZiMnN1WTI5dE1JSUJJakFOQmd
rcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBMDlUWlJrNDFNU3dJWjVobEZna01jYm1KRmkycjdPVzlKZ29uTTFmYnUxUy9aNnZBMklhZXFBVURaWVpOQ21iVzdpdDhHend0VjQrVlVMQkU3QXh0ck1VMk9YU2hjWHk4Q1ZBYmNoRDc3VE9xU0xkMjM1ZVZFM1BzTnJFa3ZGcUNPNlliV
FNGK1FRWHh6Z0pwd0FDTDNJSEdjUHMyVnJZS09vRkoyNjN3bUpwWUJ1bzFKMmhZK0VVQ0ZXcU9YQnVWNmJQRFM2RHFvSzlJMi82YXJMUTNtTEkzQ0NTVk9TV2NnTmhnU1FuaUxISzcxSi9hb1ExN2FhQ0hFRWY0WFJKMEk4ZnhkU3hJcTJsdmhoODlENXBmMlVqdjBZM0VRQ1BidHdNS1VmUzc3N0h
1cE8xaU5xbVRoVk1XWm9zQ2FOMWFHcXdSWnhUcVpIRlE2OG9lU043MzJRSURBUUFCbzRJRDR6Q0NBOTh3SndZSkt3WUJCQUdDTnhVS0JCb3dHREFLQmdnckJnRUZCUWNEQVRBS0JnZ3JCZ0VGQlFjREFqQTlCZ2tyQmdFRUFZSTNGUWNFTURBdUJpWXJCZ0VFQVlJM0ZRaUdrT01OaE5XMGVJVHhpe
jZGbTkwV3pwMFNnV0NDOWZZcmcvTFJJQUlCWkFJQkNqQ0NBZG9HQ0NzR0FRVUZCd0VCQklJQnpEQ0NBY2d3WmdZSUt3WUJCUVVITUFLR1dtaDBkSEE2THk5amNtd3ViV2xqY205emIyWjBMbU52YlM5d2EybHBibVp5WVM5RFpYSjBjeTlDVERKUVMwbEpUbFJEUVRBeExrRk5SUzVIUWt4ZlFVMUZ
KVEl3U1c1bWNtRWxNakJEUVNVeU1EQXlLRElwTG1OeWREQldCZ2dyQmdFRkJRY3dBb1pLYUhSMGNEb3ZMMk55YkRFdVlXMWxMbWRpYkM5aGFXRXZRa3d5VUV0SlNVNVVRMEV3TVM1QlRVVXVSMEpNWDBGTlJTVXlNRWx1Wm5KaEpUSXdRMEVsTWpBd01pZ3lLUzVqY25Rd1ZnWUlLd1lCQlFVSE1BS
0dTbWgwZEhBNkx5OWpjbXd5TG1GdFpTNW5ZbXd2WVdsaEwwSk1NbEJMU1VsT1ZFTkJNREV1UVUxRkxrZENURjlCVFVVbE1qQkpibVp5WVNVeU1FTkJKVEl3TURJb01pa3VZM0owTUZZR0NDc0dBUVVGQnpBQ2hrcG9kSFJ3T2k4dlkzSnNNeTVoYldVdVoySnNMMkZwWVM5Q1RESlFTMGxKVGxSRFF
UQXhMa0ZOUlM1SFFreGZRVTFGSlRJd1NXNW1jbUVsTWpCRFFTVXlNREF5S0RJcExtTnlkREJXQmdnckJnRUZCUWN3QW9aS2FIUjBjRG92TDJOeWJEUXVZVzFsTG1kaWJDOWhhV0V2UWt3eVVFdEpTVTVVUTBFd01TNUJUVVV1UjBKTVgwRk5SU1V5TUVsdVpuSmhKVEl3UTBFbE1qQXdNaWd5S1M1a
mNuUXdIUVlEVlIwT0JCWUVGSVUrbm1tdHJVMWNlS0E3aGZhUnlRWDV3UytmTUE0R0ExVWREd0VCL3dRRUF3SUZvRENDQVNZR0ExVWRId1NDQVIwd2dnRVpNSUlCRmFDQ0FSR2dnZ0VOaGo5b2RIUndPaTh2WTNKc0xtMXBZM0p2YzI5bWRDNWpiMjB2Y0d0cGFXNW1jbUV2UTFKTUwwRk5SU1V5TUV
sdVpuSmhKVEl3UTBFbE1qQXdNaTVqY215R01XaDBkSEE2THk5amNtd3hMbUZ0WlM1blltd3ZZM0pzTDBGTlJTVXlNRWx1Wm5KaEpUSXdRMEVsTWpBd01pNWpjbXlHTVdoMGRIQTZMeTlqY213eUxtRnRaUzVuWW13dlkzSnNMMEZOUlNVeU1FbHVabkpoSlRJd1EwRWxNakF3TWk1amNteUdNV2gwZ
EhBNkx5OWpjbXd6TG1GdFpTNW5ZbXd2WTNKc0wwRk5SU1V5TUVsdVpuSmhKVEl3UTBFbE1qQXdNaTVqY215R01XaDBkSEE2THk5amNtdzBMbUZ0WlM1blltd3ZZM0pzTDBGTlJTVXlNRWx1Wm5KaEpUSXdRMEVsTWpBd01pNWpjbXd3SHdZRFZSMGpCQmd3Rm9BVXo0UllmbmIrZFlHTzJ6QnJma1p
lN3BLVWx6WXdIUVlEVlIwbEJCWXdGQVlJS3dZQkJRVUhBd0VHQ0NzR0FRVUZCd01DTUEwR0NTcUdTSWIzRFFFQkN3VUFBNElCQVFCbXdUZUVCT21ZdXYvMVRWZGZvN3V3cWRydXhaKzRDaU9KOUZERlFzYVJic0VjZ1k2dVpXS0xNZmxXQ2pjTGR0UXhiVEZhMHZGTFlEZ1hBS1p0WU1xZUFJL0F1O
StEeEtKOVJ4by9UVGx5MHE2YUNleGFvemVGdmVEbENJbWV0Smo0UXppaEV3Nkp5MlV5bElVT0duT2o2SlI0cEhKSGZ5NTZTUkU4d1QvSTB5NFdoRjRJbFpoYnowMEtYaUtNMEt2Qi95Tks2V2lnc28wNUVsRkhUU1BhcWtPZm1tUC9JR0hYWWhFWlRZQ2F2eWZRWmRDNDRDb1pRY0FGdmM3NGxEcGZ
mVy8wZ1hic3l3K3ZaTXkrZEpwTlpKcWJnbFNLU0prVWVkdXlpRlBhWXc3M2VSa0IvTHk5a0hPK294M0NDQ1J2VzNNYlZZTVV2U2hrUnlETCsvU0IiLCJ4NXQiOiJreDZTT2dYWUtYbDREMEFUdERxS2ROMUtVZEUifQ.eyJuYmYiOjE2MjQ5NTg0MzMsImV4cCI6MTYyNDk1OTAzMywiaXNzIjoiMD
AwMDAwMDItMDAwMC0wZmYxLWNlMDAtMDAwMDAwMDAwMDAwQDQxZGUzZDYyLWU1MjItNDU3ZC1hZjM5LWU0YTllY2YwNjRmOCIsImF1ZCI6IjAwMDAwMDAxLTAwMDAtMDAwMC1jMDAwLTAwMDAwMDAwMDAwMC9hY2NvdW50cy5hY2Nlc3Njb250cm9sLndpbmRvd3MubmV0QDQxZGUzZDYyLWU1MjIt
NDU3ZC1hZjM5LWU0YTllY2YwNjRmOCJ9.jNcPg7h_c4qsAFMkPZxWqT1yao3FZw6sj5-4LlsPgN-I50tJuGA5LPu8b4R21DaWwGkrnVz7Q8gXYsDO8VX1UyzI6iShvv4PQBrU5iDhSOi3naX3GBu9dywtStuH789lXb-XTdcxitxGqkVFhgVhTA4GC15LRDjrGxgq6amXm7zRRl35cvM_gYqK-bh0d
FQYwKRI6SFGo5ju5a4XM5KhU0I8DbBDNmzNg00_jXuoHUz13TUCnAj_zbBGEouL0MULj3FC4rqjzCd8Zp4ELeWy9i8sbiqvd1P3tQ7xZP_8WMK3D0jk0j-kuYytOENWE8URpItfAwYbJzwQCiva8XrMGg&resource=00000002-0000-0ff1-ce00-000000000000%2fexwebservices.cloudm
enow.net%4041de3d62-e522-457d-af39-e4a9ecf064f8
Information:[TokenBuildRequest:GetActorTokenFromAuthServer] response headers was
Pragma: no-cache
Strict-Transport-Security: max-age=31536000; includeSubDomains
X-Content-Type-Options: nosniff
client-request-id: a54bb27e-1040-4459-8953-61d83af8d862
x-ms-request-id: fbb08bf6-9b74-4e8e-89ad-fa8107769600
x-ms-ests-server: 2.1.11829.8 – WEULR2 ProdSlices
Cache-Control: no-store, no-cache
Content-Type: application/json; charset=utf-8
Expires: -1
P3P: CP= »DSP CUR OTPi IND OTRi ONL FIN »
Set-Cookie: fpc=Aq9YqFGX07JGjH4Yz3S2Eokl2yrbAQAAAODcbNgOAAAA; expires=Thu, 29-Jul-2021 09:20:33 GMT; path=/; secure; HttpOnly; SameSite=None,esctx=AQABAAAAAAD–DLA3VO7QrddgJg7WevrK5LLnt3Qo0u6izu_lPbiLpb8V8baZau5fOr_f6dZAiJ
gVcrmZuBJCzIKZM6LRXJTd3vvxsy-8CpDVwwZC9BrozaMPaAtFbsyvDEAdtg14pseacRvjSqJs493e-ksN4rFuQfCgx-J9EiFC3PjQt4ELO27MI_1EcA-oalZlfq2MXQgAA; domain=.accounts.accesscontrol.windows.net; path=/; secure; HttpOnly;
SameSite=None,x-ms-gateway-slice=estsfd; path=/; secure; httponly,stsservicecookie=estsfd; path=/; secure; httponly
Date: Tue, 29 Jun 2021 09:20:33 GMT
Content-Length: 1433
Information:[ACSTokenBuildRequest:BuildToken] finished
Information:[OAuthTokenBuilder:GetAppToken] finish building apptoken; the token is {« typ »: »JWT », »alg »: »RS256″, »x5t »: »nOo3ZDrODXEK1jKWhXslHR_KXEg », »kid »: »nOo3ZDrODXEK1jKWhXslHR_KXEg »}. »oid »:
« »6768ea00-362c-495c-9e04-330cd89360e9″ » « iss »: « »00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »:
« »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624958133 » « exp »: « 1625044833 »
Information:[OAuthTokenBuilder.GetAppWithUserToken] nameid is allowed to be included in the claim set
Information:[OAuthTokenBuilder.GetAppWithUserToken] only nameid to be included in the claim: no
Information:[OAuthTokenBuilder.GetAppWithUserToken] building token with user context for the audience ‘00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8’
Information:[OAuthTokenBuilder.GetAppWithUserToken] claims count: 5
Information:[OAuthCredentials:Authenticate] send request to ‘https://exwebservices.cloudmenow.net/ews/Exchange.asmx’ with the bearer token: ‘{« alg »: »none », »typ »: »JWT »}. »iss »:
« »00000002-0000-0ff1-ce00-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »: « »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624958433 » « exp »:
« 1624987233 » ; actor: {« typ »: »JWT », »alg »: »RS256″, »x5t »: »nOo3ZDrODXEK1jKWhXslHR_KXEg », »kid »: »nOo3ZDrODXEK1jKWhXslHR_KXEg »}. »oid »: « »6768ea00-362c-495c-9e04-330cd89360e9″ » « iss »:
« »00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »: « »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624958133 » « exp »:
« 1625044833 » ‘
Token:{« alg »: »none », »typ »: »JWT »}. »iss »: « »00000002-0000-0ff1-ce00-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »:
« »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624958433 » « exp »: « 1624987233 » ; actor:
{« typ »: »JWT », »alg »: »RS256″, »x5t »: »nOo3ZDrODXEK1jKWhXslHR_KXEg », »kid »: »nOo3ZDrODXEK1jKWhXslHR_KXEg »}. »oid »: « »6768ea00-362c-495c-9e04-330cd89360e9″ » « iss »:
« »00000001-0000-0000-c000-000000000000@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « aud »: « »00000002-0000-0ff1-ce00-000000000000/exwebservices.cloudmenow.net@41de3d62-e522-457d-af39-e4a9ecf064f8″ » « nbf »: « 1624958133 » « exp »:
« 1625044833 »
Exchange Response Details:
HTTP response message:
Exception:
System.Net.WebException: The remote server returned an error: (401) Unauthorized.
at System.Net.HttpWebRequest.GetResponse()
at Microsoft.Exchange.Monitoring.TestOAuthConnectivityHelper.SendExchangeOAuthRequest(ADUser user, String orgDomain, Uri targetUri, String& diagnosticMessage, Boolean appOnly, Boolean useCachedToken, Boolean
reloadConfig), diagnostics: 2000005;reason= »The user specified by the user-context in the token does not exist. »;error_category= »invalid_user »
ResultType : Error
Identity : Microsoft.Exchange.Security.OAuth.ValidationResultNodeId
IsValid : True
ObjectState : New



It agree, a useful phrase
J’aimeJ’aime